Letscall – new sophisticated Vishing toolset
07 July 2023

Jump to
Introduction to Letscall
In recent years, the rise of Vishing, also known as Voice over IP Phishing, has become so popular that it has eroded trust in calls from unknown numbers.
Receiving calls from contacts pretending to be Bank employees is an unwelcome scenario, although the possibility that all incoming calls you receive during the day come from a fraudster is extremely high. During our daily threat-hunting activities, we came across a previously unseen group of malicious applications similar to others reported by Kaspersky.
The threat actor group behind these campaigns refers to this toolset as “Letscall”, which currently targets individuals from South Korea. Technically, there is nothing prohibiting them to extend the landscape of the attack to European Union countries. In other words, we are dealing with a ready-to-use framework which could be used by any threat actor, as it contains all instructions and tools on how to operate the affected devices and how to communicate with the victims.
The group likely consists of:
- Android developers familiar with the modern concept of VOIP traffic routing. We say “developers” as we observed command naming differences in one of the stages.
- Designers responsible for Web pages, icons, and the content for administration panel, Phishing web pages, and mobile malicious applications.
- Frontend developers familiar with JavaScript development including VOIP traffic processing.
- Backend developers familiar with techniques to secure backend API from unauthorised access.
- Call operators with voice social engineering attack skills, who can speak different languages fluently.
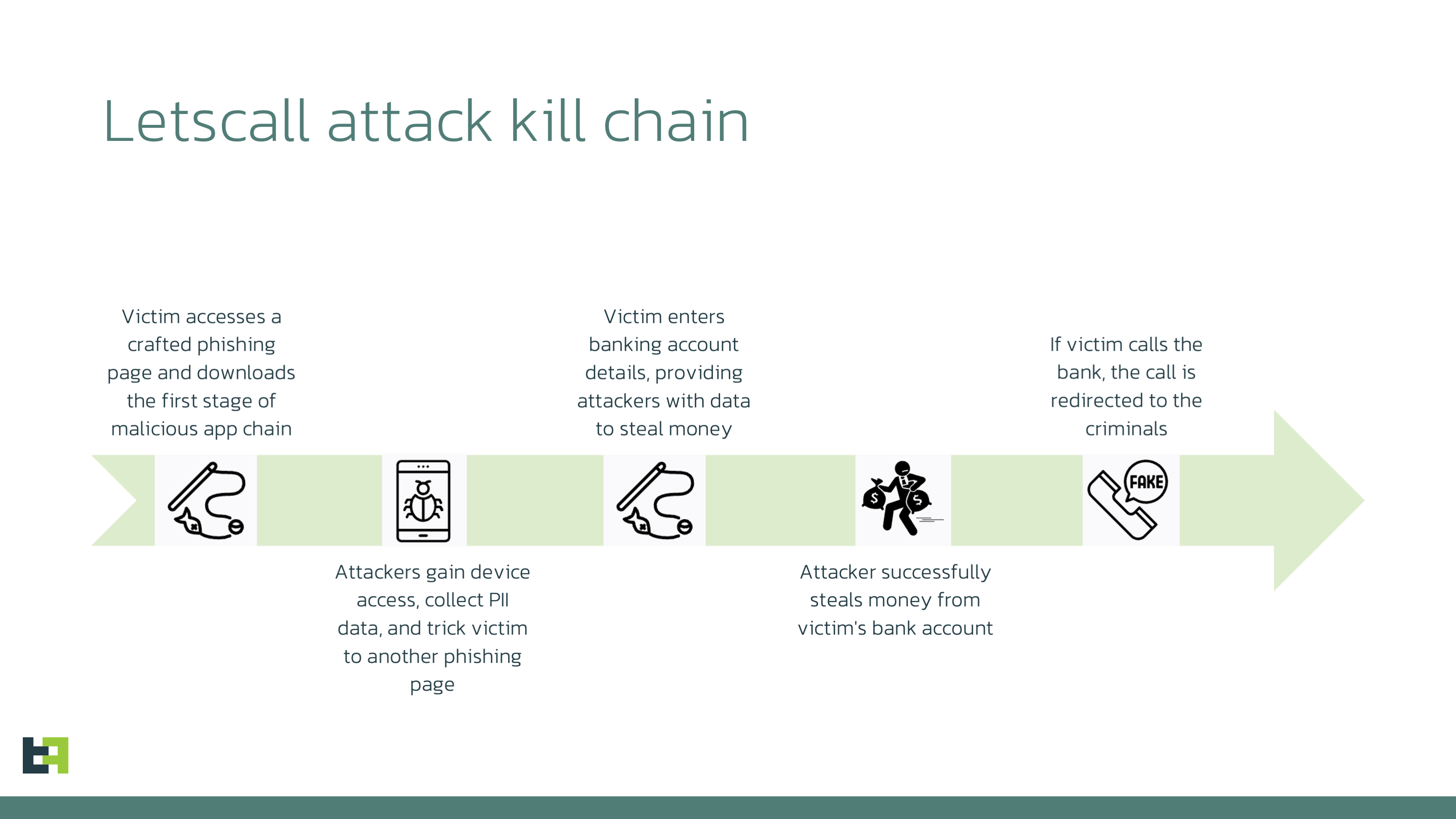
The attack consists of three stages:
The victim visits a specially crafted phishing web page that looks like Google Play Store. From that page, the victim downloads the first stage of the malicious applications chain.
- This first stage (we will call it the downloader) runs preparations on the device, obtains the necessary permissions, opens the phishing web page, and installs the second stage malware, which will be downloaded from the control server.
- The second stage is a powerful spyware application that will help the attacker to exfiltrate data as well as to enrol the infected device into the P2P VOIP network used to communicate with the victim using video or voice calls. This application also drops a third stage, the next piece of the chain.
Letscall uses WEBRTC technology to route the VOIP traffic and to connect the victim with call-centre operators. To achieve maximum phone or video call quality and to overcome NAT and firewall, Letscall uses STUN/TURN methods, including Google STUN servers. - The third stage is a companion application for the second stage malware and extends some functions: it contains phone call functionality, used to redirect the call from the victim device to the attacker call centre.
Vishing evolves
Such Vishing attacks have evolved to become more technical and sophisticated as fraudsters now use modern technologies for voice traffic routing and systems that automatically call the victim (so-called auto-informers that are used for automating advertisement through phone calls), and play pre-recorded lure messages. If the victim takes the bait, a phone call operator will pick up the call and guide the victim to act in the way the fraudster wants. An attacker might trick a victim to go to the nearest ATM to withdraw cash or push the victim to disclose personal information such as banking account data, credit card details, or banking credentials.
Such attacks have become a clear trend over the past few years and there is no evidence that fraudsters will decrease the pressure.
Nowadays, both victims and the security industry have evolved and are fighting this kind of attack with a wide variety of defense mechanisms. The use of caller identification applications or the knowledge of fraudster tactics may be enough to defend against attackers.
This is probably one of the reasons why fraudsters try to gain trust from the victim using any kind of information that they have, not only using name and phone number. To achieve a higher level of trust, attackers perform reconnaissance on the victim, by gaining access to the victim device.
Pairing the two types of attacks (mobile phone infection together with Vishing), fraudsters can “kill two birds with one stone”: a common type of attack we have observed consists of requesting a micro-loan behind the back of the victim. In case the victim notices some unusual activity, the attacker will call the victim, posing as a member of the Bank security team, and reassure the victim that there is nothing to worry about.
With full control of the infected device, the attacker will also reroute any call to a different call centre managed by the criminals. A well-prepared operator will answer the call in case the victim decides to contact the bank and ask questions related to suspicious activity. With this Modus Operandi, attackers may also ask the victim for additional details that could help them in their criminal activities and complete the fraudulent money transfer.
This kind of attack is extremely dangerous as victims must then pay the loan back, and financial institutions may not care about such attacks and device infections, decreasing the possibility of investigating potential fraud. This is the reason why such an attack should be disclosed and reported by the industry.
For all three stages of "Letscall" malware, attackers used strong evasion techniques. Some versions of the downloader were secured using Tencent Legu obfuscation or using Bangcle (SecShell). For the second and third stages, long names in the ZIP file directory tree and manifest corruption techniques were used. The same techniques were recently reported by Checkpoint. However, the campaigns are different from a code and infrastructure point of view. It is possible that criminals share knowledge with each other or are influenced by other actors in the same region.
“Letscall” second and third stages are huge and our research is still ongoing. However, we would like to provide some insights right now.
The Downloader
There is no clue as to how an attacker could convince a victim to visit the decoy web page where the Downloader could be found, it might be a Black SEO technique or social engineering using spam. So far, we know that those pages mimic the Google Play store and are optimised for mobile screen resolution. A notable detail here is the language of the page – Korean.
In the meantime, under the hood of the web page, we can observe the script with comments in a different language – Chinese.
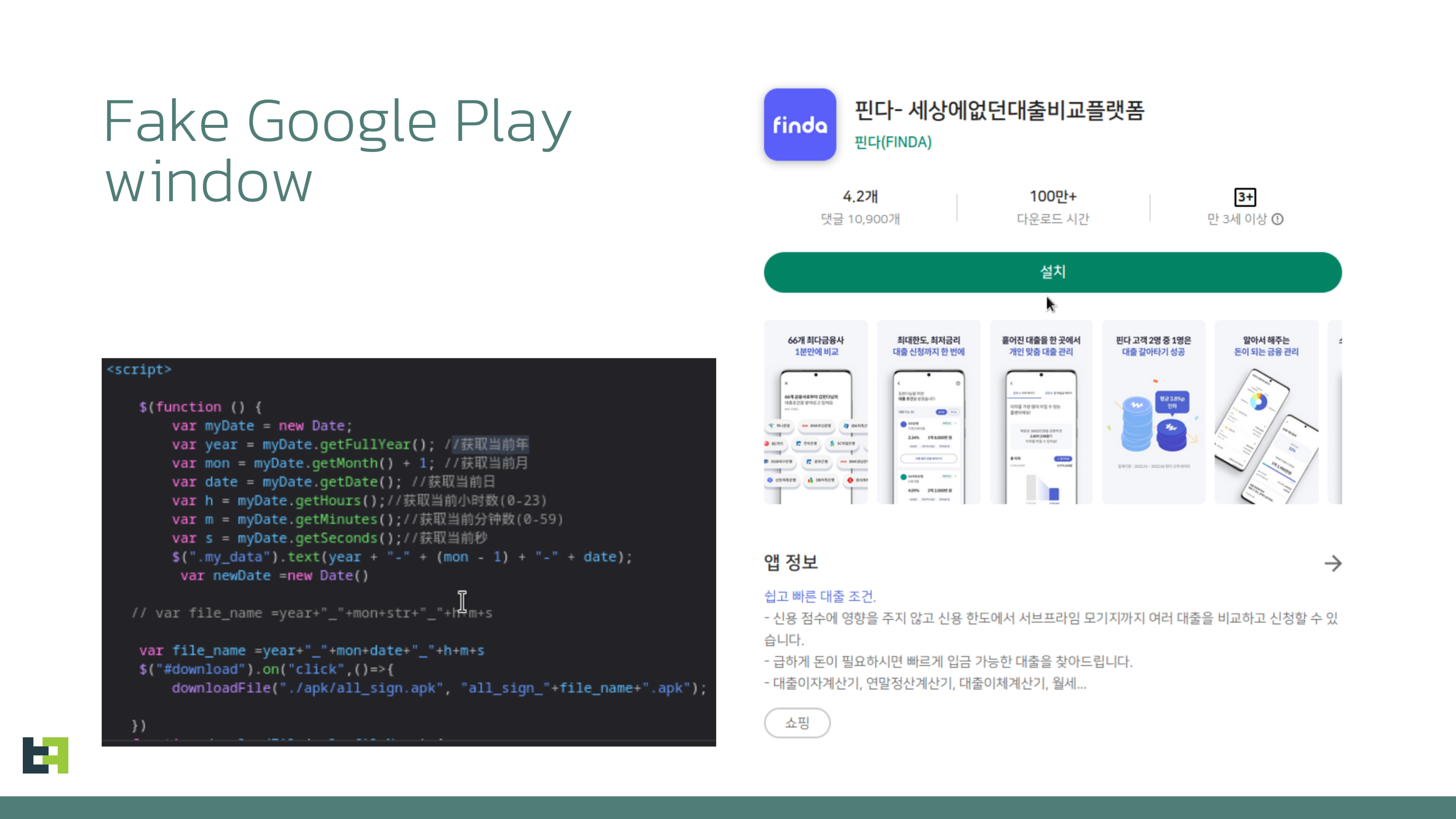
From a technical point of view, the Downloaders used are relatively simple applications, sometimes using custom techniques that we will describe later. The Downloaders aim to do two things:
- Download and run the second stage application. The URL address of the payload is hardcoded into the application.
- Open a web view with a phishing window which is also hardcoded into the application.
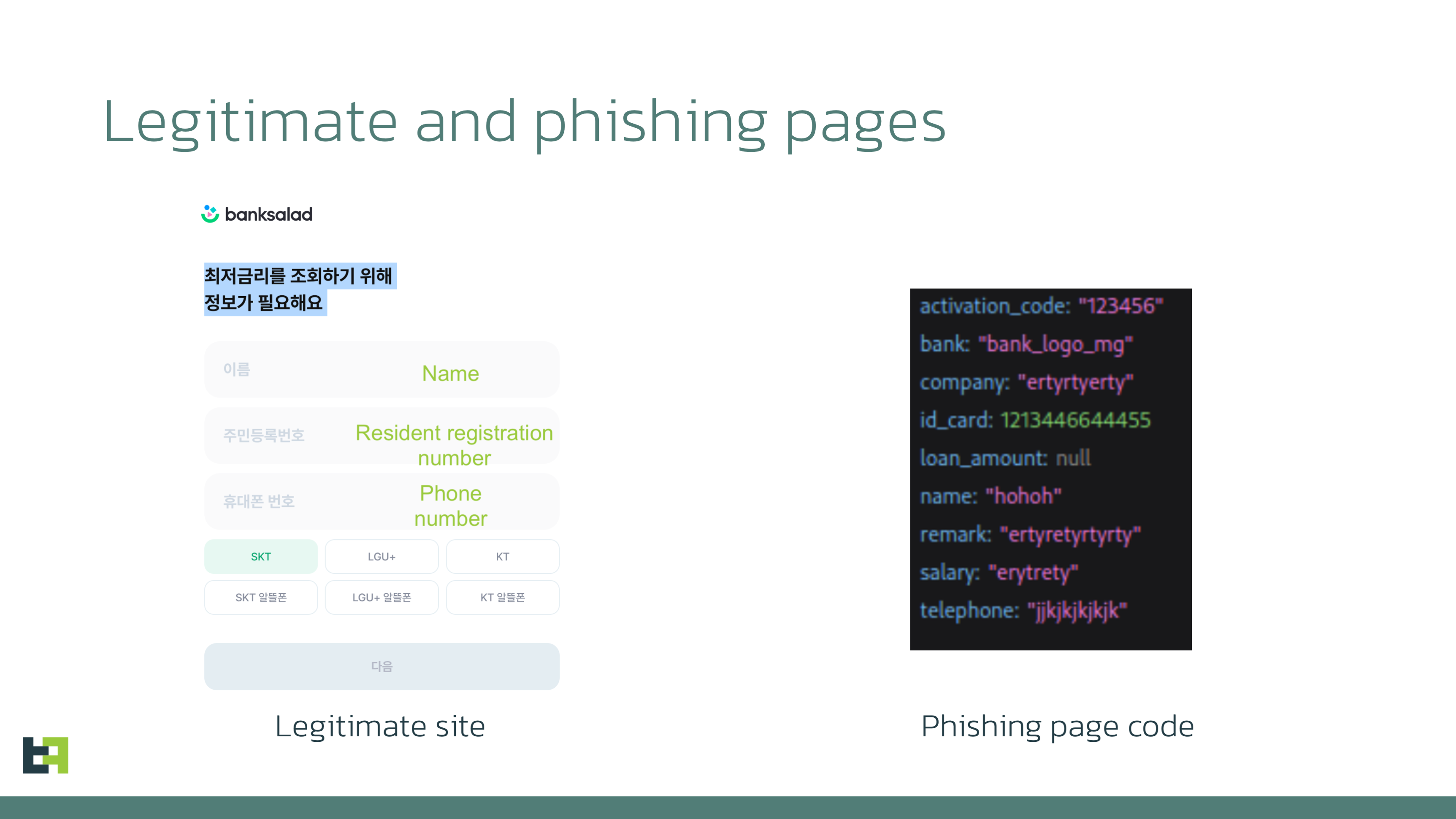
These pages differ depending on which distribution campaign is ongoing. We saw at least three pages which were mimicking Banksalad (Loan comparison aggregator), Finda (loan comparison aggregator) and KICS (Korea Information System of Criminal-Justice Services)
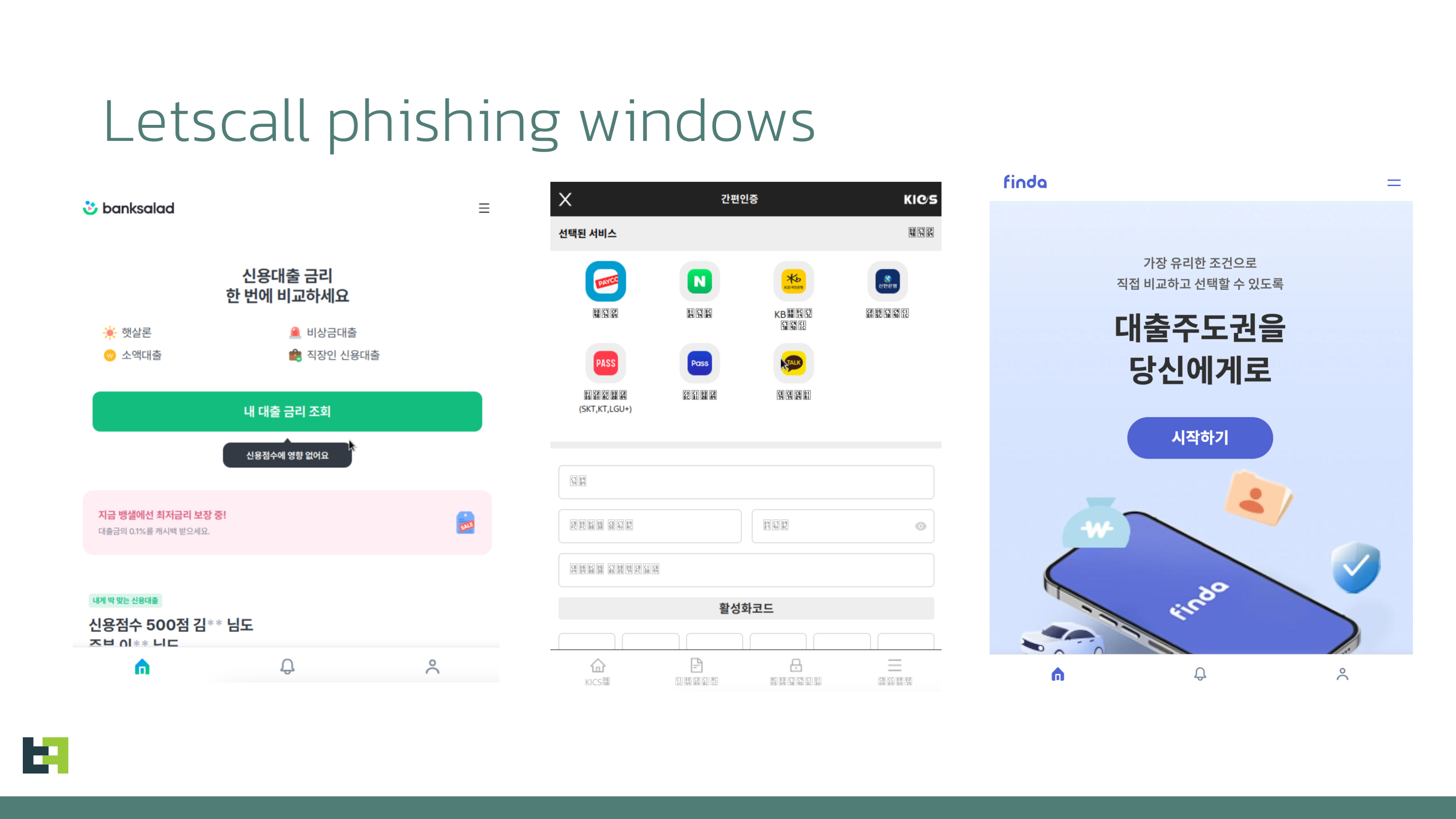
Each page will trick the victim to type in sensitive information, such as Resident registration number (or ID), phone number, home address, salary size, and employer name. That input data will be automatically sent to the attackers.
The same data is supposed to be typed into the original web page of the loan aggregator. We can say with high confidence that attackers will either use the exfiltrated data to fill a similar form on the legitimate website to request a loan, or it might also be possible that the phishing page is acting as a proxy between the victim and loan aggregator page:
Second stage
At first glance, it seems clear that the application is extremely obfuscated, and it will take a long time to analyze its functionalities. Let’s uncover each technique:
- The APK files contain long path names inside. Some analysis systems will not be able to process the extraction of content of such APK files.
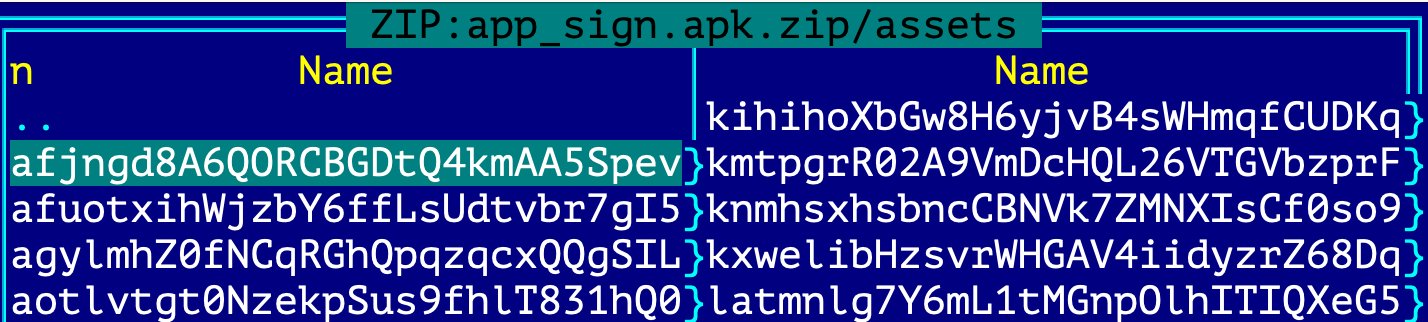
- XML file corruption.
- Code packing: The core DEX file does not contain the code that is listed inside the manifest. However, it contains obfuscated code that will collect files from the APK, decrypt them and load them. Those files are located in the root of the APK file, and their names start with “o” and end with “bf” which is “obf” or obfuscation:
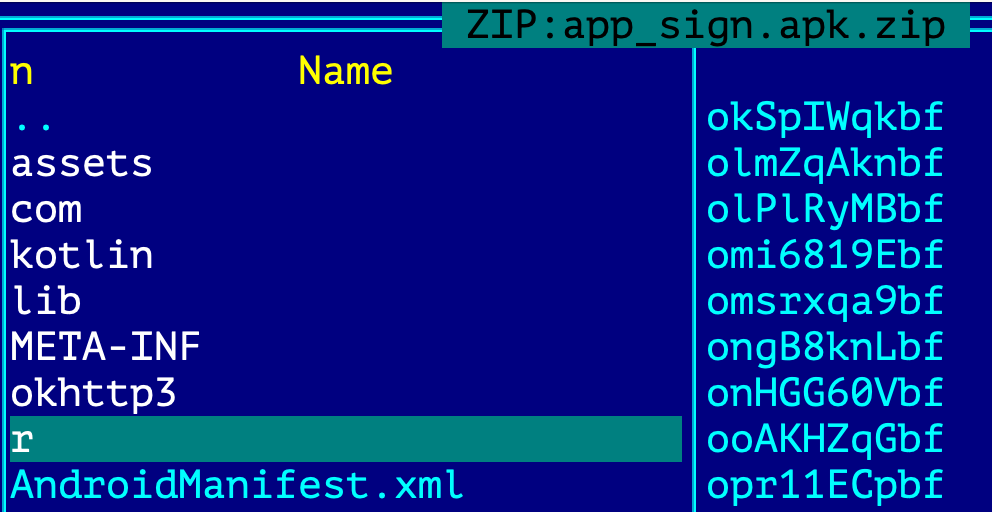
All the files had a similar header and relatively low entropy.
Even some strings were revealed:
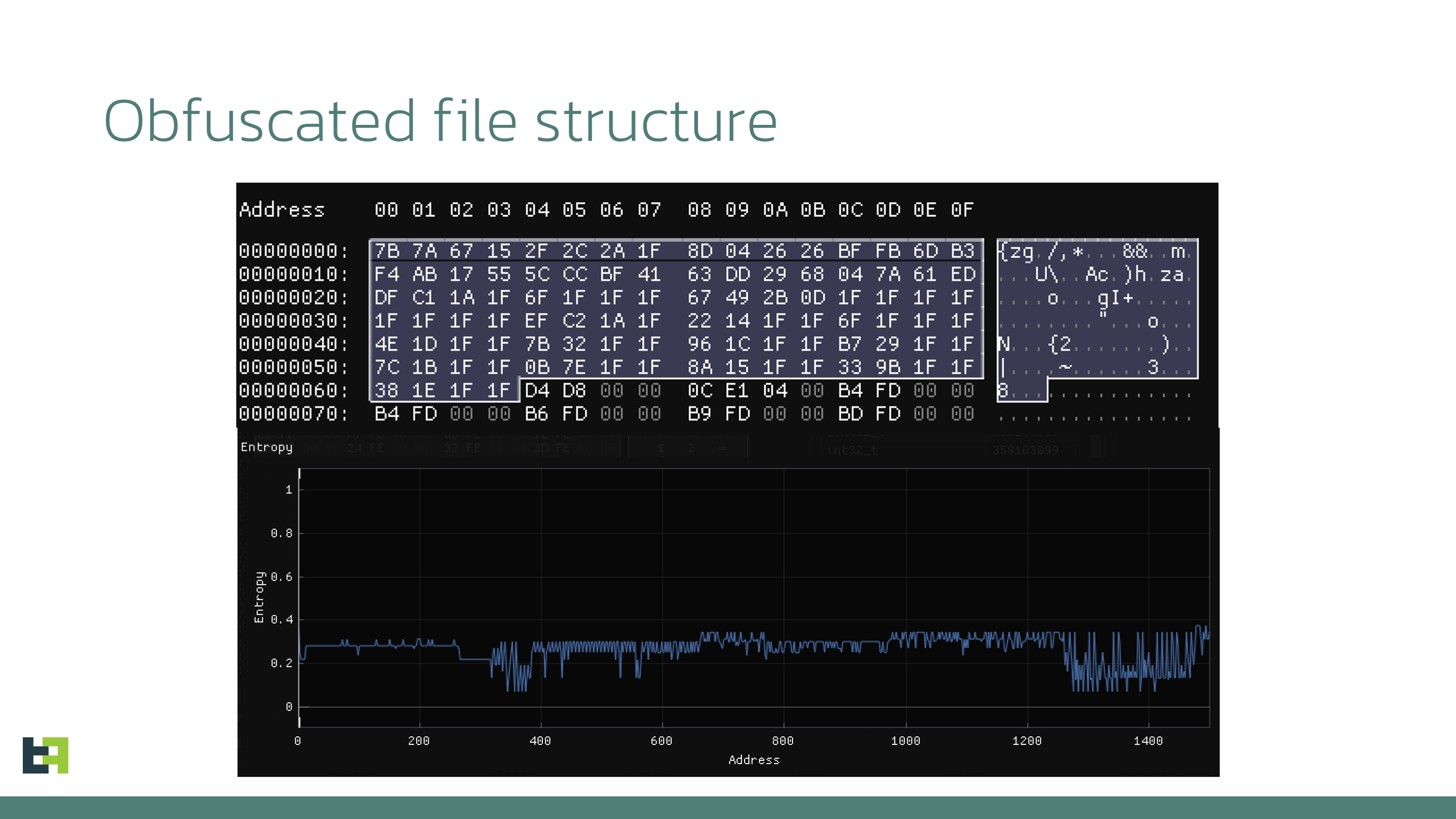
After some tinkering, it became obvious that all these dozens of files were DEX files with minor changes in their headers. By observing the repeating 0x1f value in the first bytes of the file, we can guess that to hide the original header one-byte XOR encryption was used and only 0x64 bytes of the files were encrypted.
We reconstructed the APK file and were able to analyse the code. Right after the first analysis steps, we realised that we faced with something big.
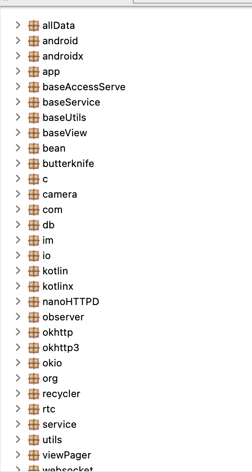 The resulting APK file was based on a dozen different frameworks including popular ones like okhttp3 and butterknife, as well as some libraries that we observed for the first time.
The resulting APK file was based on a dozen different frameworks including popular ones like okhttp3 and butterknife, as well as some libraries that we observed for the first time.
The most interesting library is im/zego.
The second stage abuses the legitimate service ZEGOCLOUD as a provider for Voice over IP communication and messaging. To handle such communications, which rely on WEB RTC, actors use relay servers. The specifically used publicly available STUN/TURN servers including servers from Google, together with self-configured servers. In the process, they also leaked the credentials inside the application code.

Such functionality is needed to perform P2P voice/video connection between the call-centre operator and victim, and the same channel is also used for C2 communication with many different commands. In addition, the malware also supports communication using web sockets. Commands that come from P2P service and web socket communication sometimes duplicate each other.
We will describe each command in the Appendix section of this report. However, one command is quite interesting:
“zego”: this command, depending on the arguments, will stop or start video streaming. This way the “Letscall” operator will communicate with the victim using a video camera and microphone.
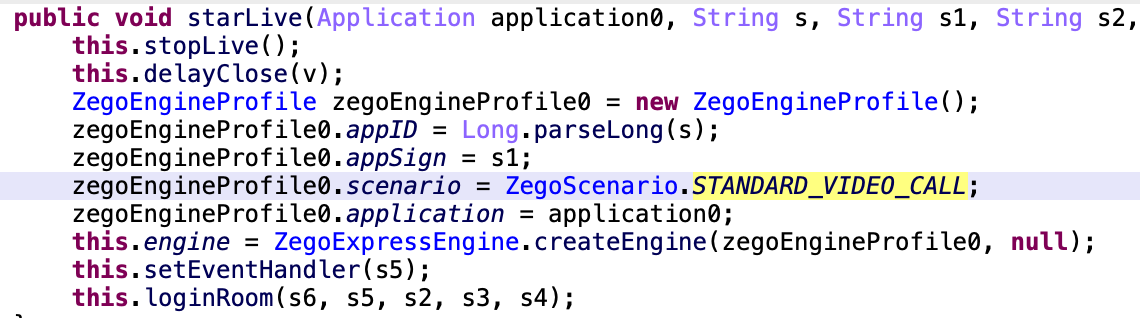
The remaining 32 commands relate to
- device fingerprinting
- victim location tracking
- data exfiltration
- infection footprints cleaning
To exfiltrate data and change configuration the malware uses traditional http communication: 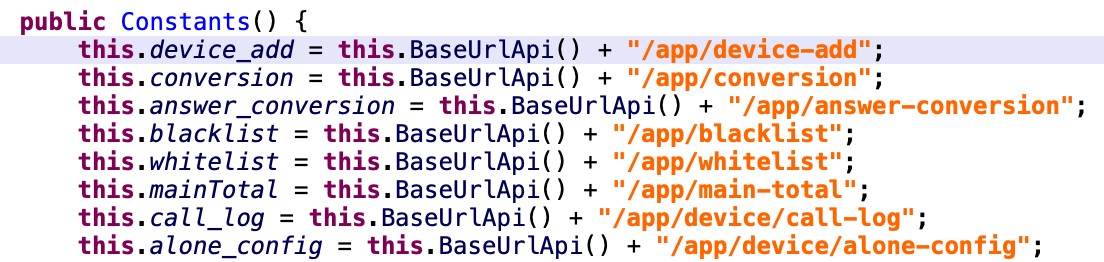
An attacker can also configure a whitelist for the phone numbers that should be redirected and a blacklist for those numbers that should bypass the redirection.
Another interesting thing that we noticed is the use of nanoHTTPD. This application creates a local http server and then opens the Chrome browser to access it.
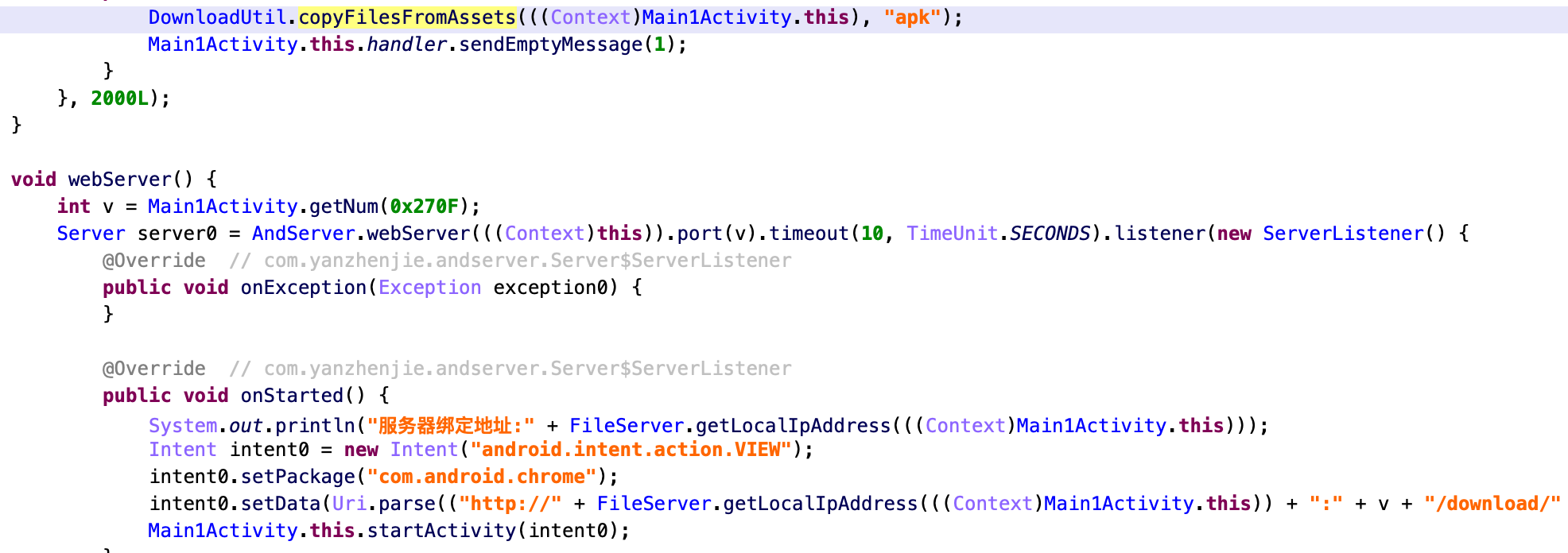
By abusing the accessibility services, it will push the necessary interface elements inside of Chrome and deliver the third-stage malware to the victim. This more complicated method is used to trick victims in a more effective way and convince them that nothing suspicious is happening.
Third stage
From a technical point of view, the next APK file that is installed looks very similar to the Second stage APK: the same evasion techniques are used, and the same XOR-encrypted DEX files are in the root folder of the APK file. This application also contains a large code base:
 The most interesting part of the Third stage is the package called “phonecallapp”: this package contains code responsible for the phone call manipulation attack; it will intercept incoming and outgoing calls and reroute them according to the desire of the attacker.
The most interesting part of the Third stage is the package called “phonecallapp”: this package contains code responsible for the phone call manipulation attack; it will intercept incoming and outgoing calls and reroute them according to the desire of the attacker.
To configure the way phone calls should be processed, attackers use a local SQLite database with the following structure:
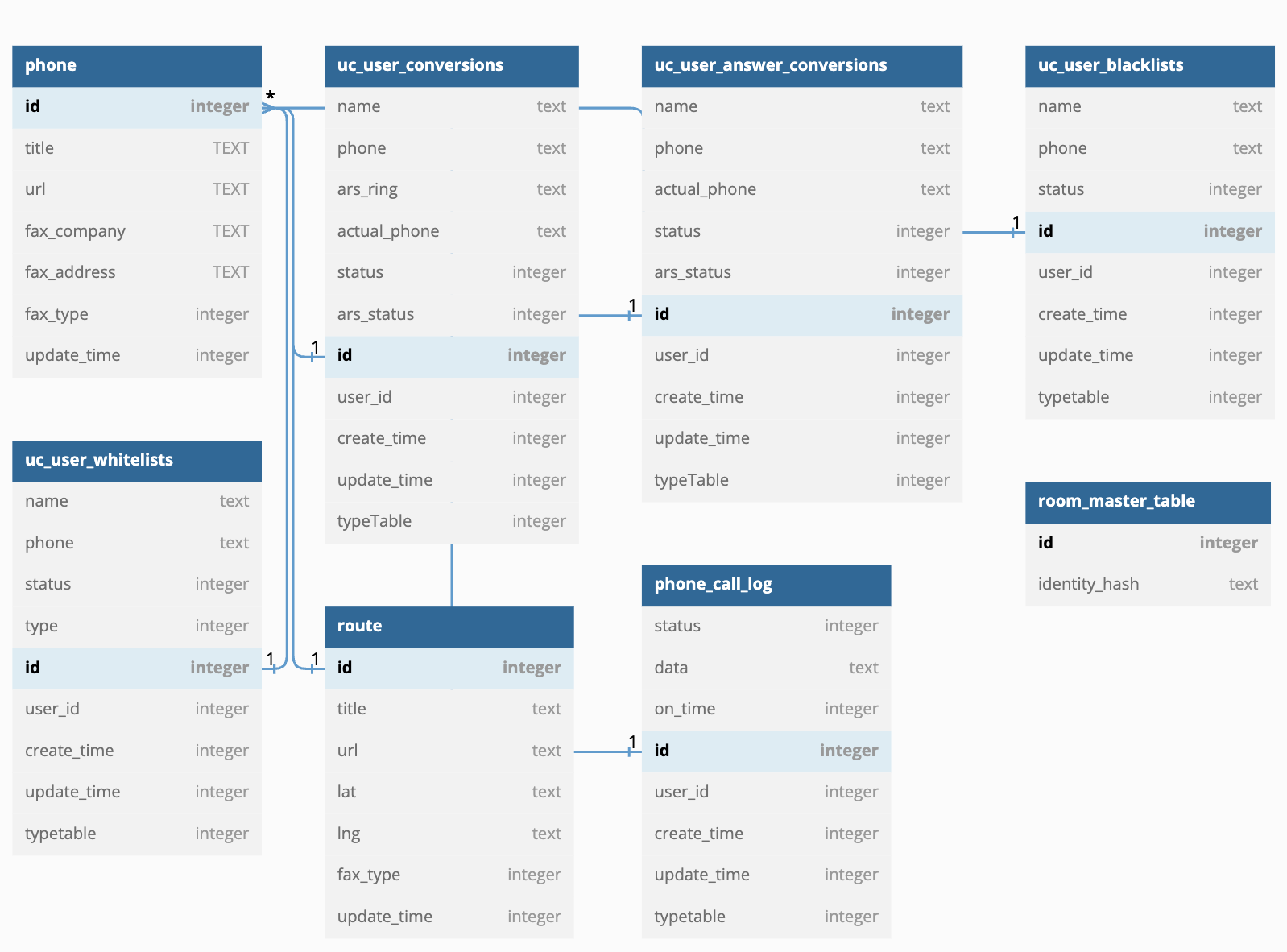
Among the assets of the third stage APK, there are already prepared MP3 voice messages which will be played to victim in case of outgoing bank call attempts.
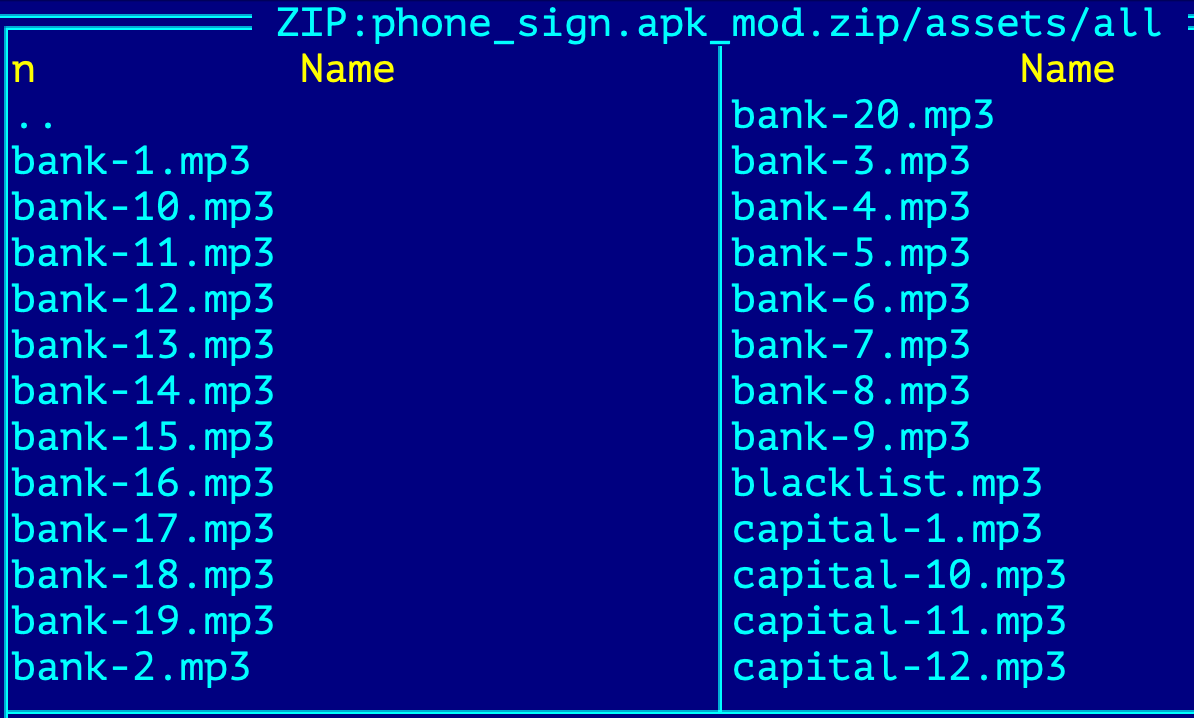 Here is the transcript of one of these mp3 files (bank-1.mp3), translated from Korean to English:
Here is the transcript of one of these mp3 files (bank-1.mp3), translated from Korean to English:
“Hello, this is Hana Bank. For ... Press 1 for remittance to Hana Bank, 2 for remittance to another bank, and 3 for transaction details. For credit card connection, press 6 for other services.”
In other words, these files are prerecorded messages aimed at guiding a caller to the best operator from the bank best suited to address their concerns. For criminals, the objective is obviously to mimic the experience that a customer would have when calling his/her bank. Together with these files, there are more mp3s that imitate DTMF dialling codes, simulating the sounds that a victim would produce by pushing on dialling pad numbers.
The third stage has its own set of commands, which also includes Web socket commands.
Some of these commands relate to the manipulation of the address book, such as creating and removing contacts. Other commands relate to creating, modifying, and removing the filters that determine which calls should be intercepted and which should be ignored. The description for each command will be provided in the Appendix section of this report.
The infrastructure
| Domain |
IP |
ASN |
| finda.letscall[.]ltd |
143.92.34[.]8 |
AS64050 |
| salad-3.letscall[.]today |
143.92.34[.]8 |
AS64050 |
| finda-msg.letscall[.]ltd |
143.92.34[.]8 |
AS64050 |
| salad-msg.letscall[.]today |
143.92.34[.]8 |
AS64050 |
| salad-h5.letscall[.]today |
143.92.34[.]44 |
AS64050 |
| finda-h5.letscall[.]ltd |
143.92.34[.]44 |
AS64050 |
| finda.letscall[.]fyi |
137.220.142[.]149 |
AS64050 |
| letscall.fss-app[.]live |
35.243.122[.]211 |
AS396982 |
| kics-h5.letscall[.]fyi |
137.220.142[.]160 |
AS64050 |
| konan-h5.finda[.]buzz |
154.215.238[.]195 |
AS134175 |
| konan.nicetv[.]live |
137.220.179[.]112 |
AS64050 |
| finda-dl.finda[.]buzz |
45.43.215[.]98 |
AS46261 |
| lets-dl.finda[.]buzz |
45.43.215[.]106 |
AS46261 |
| org-fin19.letscall[.]ltd |
143.92.34[.]22 |
AS64050 |
Right after we obtained the Downloader, we started to analyze C2 servers and revealed the admin panel.

Like many different WEB applications, it consists of two parts.
- A Frontend, based on VueJS, and used to visualize the content to the Threat Actor.
- A Backend, based in Laravel PHP framework, that communicates with frontend and malicious applications using the API.
The frontend is the most interesting part as it contains a fully functional working account for administrators as well as for phone call operators. From this panel, a phone call operator can choose the victim and start the video/audio conversation directly from the browser. The operator will also be able to see the full list of details exfiltrated from the target and uploaded to the infrastructure. It consists of at least 33000 strings of code and is massive in size if compared with other panels that we previously observed.
We identified at least 19 menus which are related to infected device control that the operator can use: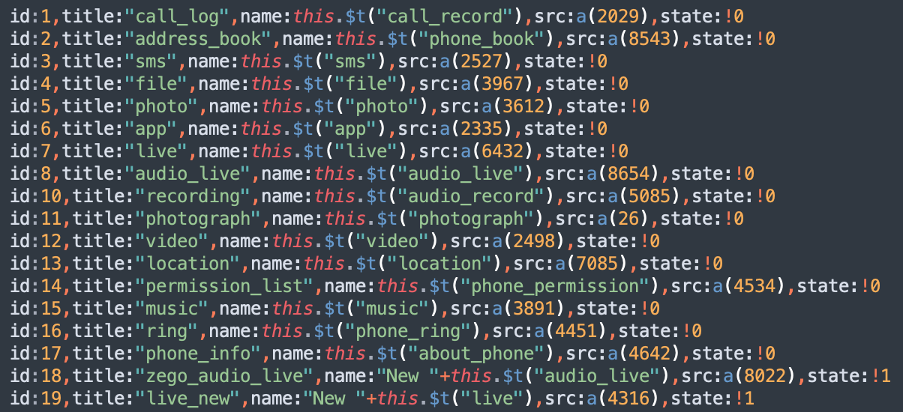
This JavaScript application will use the same VOIP infrastructure as both stages’ applications, and these servers are listed on the admin panel configuration file:
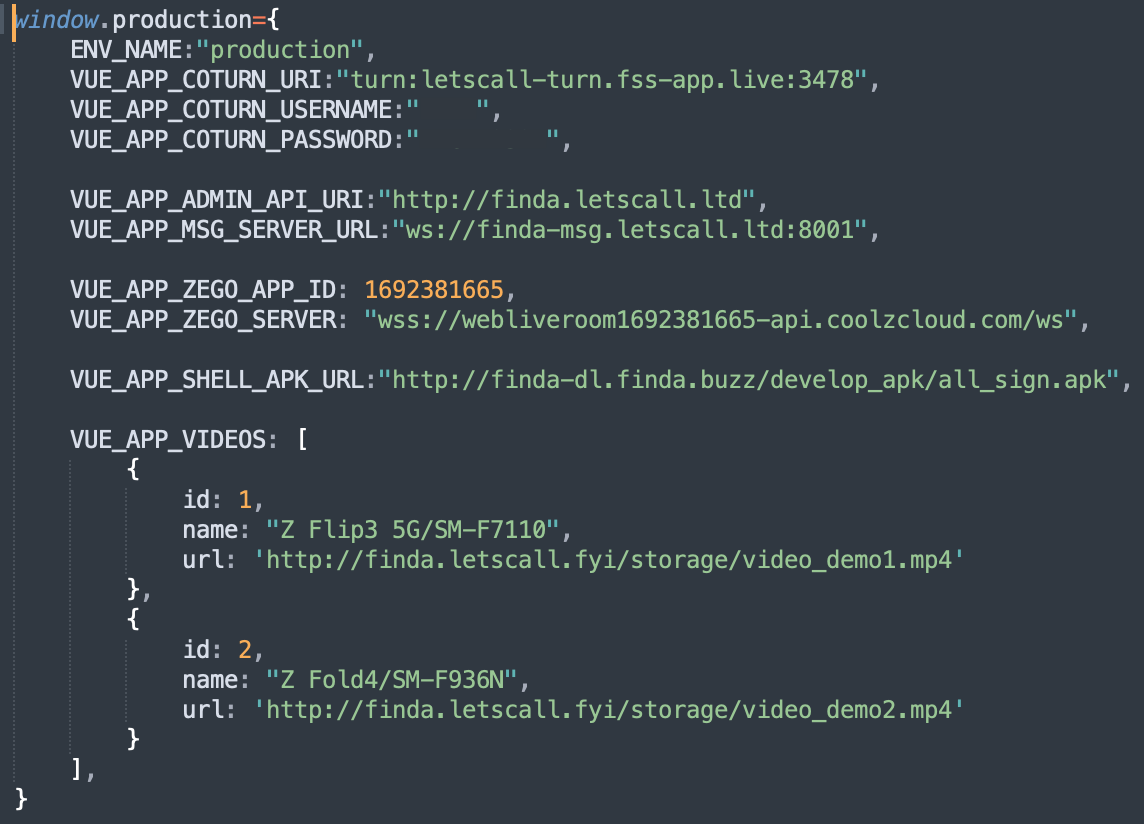
It is worth noting that the frontend app contained so-called tutorials and demos. ThreatFabric was able to download two of them. In these videos, we can observe the full infection chain and how it happens in the wild. They are probably created to facilitate the phone call operators, showing them the infection process from the point of view of a victim, and allowing them to be able to respond to questions that may arise from the victim.
After analysing the frontend panel, we came across the various APIs of the backend. Actors divided them into two main categories:
- admin – APIs responsible for managing the access to the admin panel of the operators,
- sys-user – APIs responsible for retrieving data from the backend infrastructure and controlling infected devices.
The full list of the backend API will be provided in the Appendix section of this report.
The Admin panel code also revealed some images and audio files. Audio files are the same as we saw in the Third stage application.
Images on the other hand gave us some additional details about the panel, such as that four languages are probably supported: English, Korean, Japanese, and Chinese.

Some of the images contained meta-information such as the time they were created (2022-12-02 15:22). Also, a time zone was provided: +8. This time zone corresponds to South Asian countries, including China.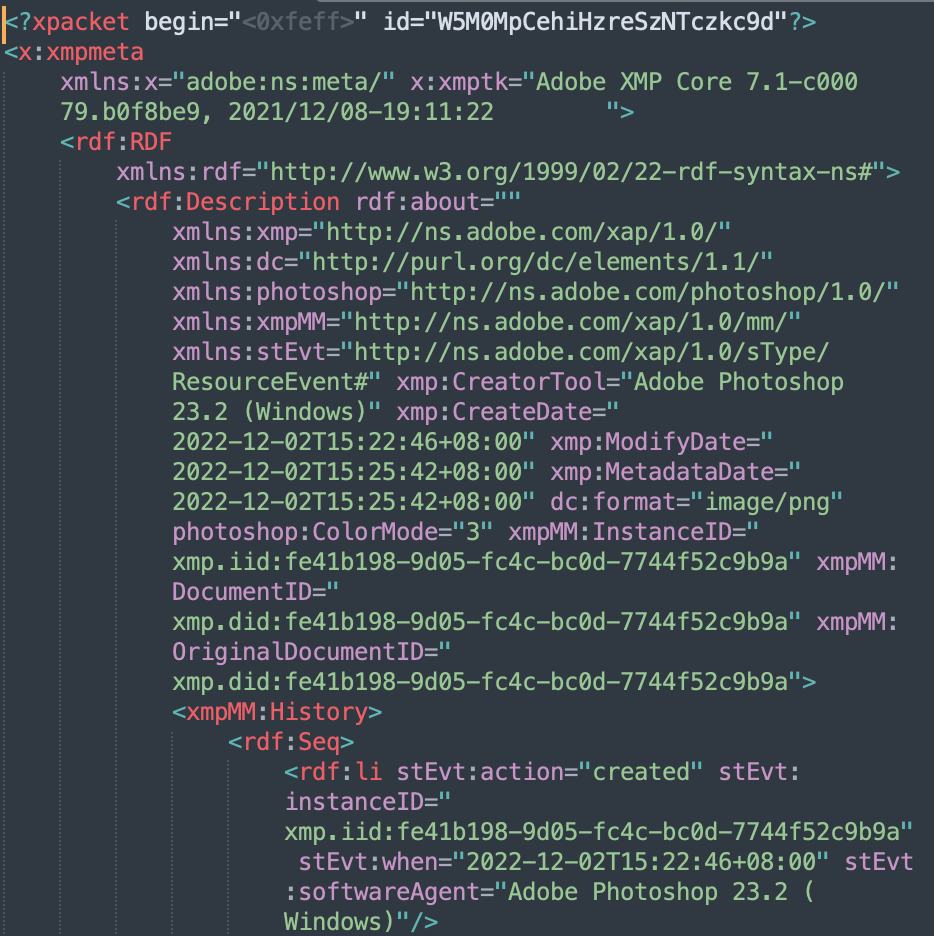
We also observed several names of the South Korean financial institutions that we predict will be used during the attack.
Conclusions
After analysing the “Letscall” malware campaigns, we came across a cybercrime group that is familiar with Android security and modern voice routing technologies. The group proved that technically well-designed social engineering attacks can still be extremely dangerous.
It is clear that technical features are as important as social engineering, which is confirmed by the attention the group dedicates to using fake Google Play pages, stolen logos of the existent Korean applications, combined with a new technique with nanoHTTPD to drop the payload.
Resident registration number (or ID) theft is able to open many doors for cybercriminals, and we see this attack vector only increase with the adoption of more and more electronic ID solutions by governments and both private and public institutions. The re-utilization of the same evasion technique used by other actors is common in Asian threat groups. They may not be sitting next to each other in the same office building, but it is possible that some developers work for multiple cybercrime groups in one region.
From a network analysis perspective, it was interesting to observe another way to control the botnet and hide traffic inside WEB RTC services. This highlights the fact that such traffic should always be analyzed by protection systems, regardless if private or Google STUN servers were used.
Regarding the “Letscall” applications, we have discussed multi-functional spyware which was designed with close attention to video and audio connection with the victim, as well as intercepting communications such as SMS, and phone calls. Location tracking was also one of the main points of contact for the cybercriminal group. Based on the many different features included in its code, Letscall could be classified as a RAT. Together with spyware functionality, RAT allows the attacker to know everything about the victim and perform efficient social engineering attacks.
Finally, the well-designed infrastructure that we observed during our analysis could potentially be used by phone operators speaking different languages. We predict that such a tool kit could be promoted as MaaS (Malware as a Service) on the Darkweb.
In order to stay safe against this campaign, we are confident that it is required to deny accessibility services access to any suspicious applications. Without this permission, it will be much harder for criminals to act on the device.
As a financial organisation, you are welcome to contact us if you suspect some app to be involved in malicious activity. Please feel free to reach our Mobile Threat Intelligence team. We will provide additional details and help with reporting the malicious app if identified: mti@threatfabric.com.
Fraud Risk Suite
ThreatFabric’s Fraud Risk Suite enables safe & frictionless online customer journeys by integrating industry-leading mobile threat intel, behavioural analytics, advanced device fingerprinting and over 10.000 adaptive fraud indicators. This will give you and your customers peace of mind in an age of ever-changing fraud.
Appendix
Indicators of compromise
File sha256 hashes
Downloader
a522a039ec619a60618c2c8a9e65adb0ff6105b655c1f9b3796e52e0d25958cb
Second stage
22109901f8290dc2319bd9b49e6bf71f9ddc1af482ddb67fc6e1c3b09ecad9c8
Third stage
bf5259bf53e3747d37d21dbf43b54ff8fa3c57fc991b53fcd320658b6cf34db9
Domains and Ips
finda.letscall[.]ltd
salad-3.letscall[.]today
finda-msg.letscall[.]ltd
salad-msg.letscall[.]today
salad-h5.letscall[.]today
finda-h5.letscall[.]ltd
finda.letscall[.]fyi
letscall.fss-app.live
kics-h5.letscall[.]fyi
konan-h5.finda[.]buzz
konan.nicetv.live
finda-dl.finda[.]buzz
lets-dl.finda[.]buzz
letscall.39nat[.]com
org-fin19.letscall[.]ltd
137.220.142[.]149
137.220.142[.]160
137.220.179[.]112
143.92.34[.]22
143.92.34[.]44
143.92.34[.]8
154.215.238[.]195
35.243.122[.]211
45.43.215[.]106
45.43.215[.]98
Second stage commands
Web Socket command list
| Command |
Description |
| CHECK_DEVICE_STATUS |
Retrieve the device information such as power level, device_id, Cell operator name via POST query to C2 |
| GET_CHECK_DEVICE_STATUS |
Retrieve the device information such as power level, device_id, Cell operator name via web socket connection |
| closeRoute |
Stop tracking location of the victim |
| deleteApp |
Delete specified application |
| deleteItemSMS |
Delete specified SMS message |
| deleteSMS |
Delete a list of SMS messages |
| getAppData |
Get the list of installed application including system applications |
| getDirTree |
Get the specified directory tree including file and subdirectories names, sizes, MD5 file hashes, last modification dates. |
| getImageAll |
Get all image pictures from SD card and upload them to server as BASE64 encoded text using POST query to C2 |
| getImageDir |
Upload the images that were observed on specified path via web socket |
| getLocation |
Get current location |
| getMusicData |
Get audio files information including Singer name, File path, Song Duration, Music file Size, MD5 music file hash, Date added, Album Id |
| getPermission |
Check if SMS permission were granted to the spyware (android.permission.READ_SMS", "android.permission.SEND_SMS", "android.permission.RECEIVE_SMS") |
| getPermissionApp |
Get the list off all permission that were granted by the application |
| getPhotoGraph |
Take a photo of front or back camera or upload last made camera shot. |
| getRecording |
Start recording microphone or upload recording to the C2 |
| getRingData |
Get information about ringtone files including MD5 hash for different type of notifications (ringtone, notification, and alarm ringtones) |
| getRoute |
Start the location tracking |
| getRouteList |
Get specified location tracking log |
| getSMSData |
Insert a message with specified text and number into the list of sent SMS messages and mark in as read |
| getSMSDataList |
Get a list of all SMS messages |
| getSMSDataListRight |
Get a list of all SMS messages |
| getSMSDefault |
Check wherever second stage have the default SMS manager permission and check if third stage installed |
| getSearchSMS |
Search for specific SMS message and send the results to web socket C2 |
| getVideoData |
Get a list of video files information including Title, Duration, Video file Size, MD5 video file hash, Date added, height and width |
| isRoute |
Check if location tracking in on/off |
| isSMS |
Turn on/off SMS interception |
| openApp |
Restart second stage or third stage |
| refresh |
Reset and restart second stage |
| searchApp |
Search for specific package among installed applications |
| sendSMSData |
Send SMS message to the specified number and with specified text |
| setPermission |
Check if Bluetooth permission granted |
| zego |
Perform a Zego video call and login into Zego room with specified parameters |
P2P service command list
| Command |
Description |
| getDirTree |
Get the specified directory tree including file and subdirectories names, sizes, MD5 file hashes, last modification dates. |
| ___download_file___ |
Upload specified file from the victim device to the C2 |
| getPermission |
Get the list of granted permissions |
| setPermission |
Turn Bluetooth adapter on/off |
| downloadFile |
Download file to the victim device |
| uploadFile |
Upload specified file from the victim device to the C2 |
| getImageAll |
Get all image pictures from SD card and upload them to server as BASE64 encoded text using POST query to C2 |
| getImageDir |
Upload the images that were observed on specified path via web socket |
| getImageBase64 |
Upload one BASE64 encoded file with specified path to the C2 |
| deleteFile |
Delete a specified list of files |
| getRecording |
Start recording microphone or stop it and upload resulting recording to the C2 |
| getAboutPhone |
Get device fingerprint |
| getRoute |
Start the location tracking |
| isRoute |
Check if location tracking in on/off |
| closeRoute |
Stop tracking location of the victim |
| getLocation |
Get current location |
| getRouteList |
Get specified location tracking log |
| getAppData |
Get the list of installed application including system applications |
| getDeviceData |
Get device information such as Device ID, Model, Operator name, Android version, power level, Network type (WIFI or cellular), Bluetooth status. |
| getMusicData |
Get audio files information including Singer name, File path, Song Duration, Music file Size, MD5 music file hash, Date added, Album Id |
| getPhotoGraph |
Take a photo of front or back camera or upload last made camera shot. |
| getRingData |
Get information about ringtone files including MD5 hash for different type of notifications (ringtone, notification, and alarm ringtones) |
| getVideoBase64 |
Upload BASE64 encoded video file with specified path to C2 |
| getVideoData |
Get a list of video files information including Title, Duration, Video file Size, MD5 video file hash, Date added, height and width |
| playVideoDetail |
Play specified video file |
| changeVideoCamera |
Switch camera that will be used for video calls |
| deleteApp |
Delete specified application |
Third stage commands
| Command |
Description |
| SAVE_CONVERSION |
Insert the fake communication history |
| getAddressBook |
Exfiltrate the address book of the victim |
| addWhitelist |
Add the phone number to Whitelist database, all calls to/from that number will be redirected to the attacker |
| callStatusChange |
Enable/disable call Whitelisting |
| getWhiteList |
Get Whitelist information |
| SAVE_DEVICE_ALONE |
Update the Third stage configuration |
| addContacts |
Add or update contact information in victims Address book |
| SAVE_BLACK |
Add the phone number to Blacklist database, all calls to/from that number will be ignored by the spyware |
| DELETE_BLACK |
Delete from Blacklist using specified list of phone numbers or contact names |
| getAddressBookDefault |
Search for specific contact inside the Address book of the victim |
| whiteDelete |
Delete from Whitelist using specified list of phone numbers of contact names |
| SAVE_ANSWER_CONVERSION |
Insert the fake communication history |
| openApp |
Restart Downloader, Second stage or Third stage |
| getPermission |
Get a list of granted permissions |
| PHONE_END_CALL |
Immediately end ongoing call |
| editWhitelist |
Update Whitelist entry |
| DELETE_CONVERSION |
Delete conversation history by specified ID from default Phone database of the victim |
| UPDATE_CONVERSION_ACTUAL_PHONE |
Update the phone number for the contact |
| answerStatusChange |
Enable/disable phone calls answering by Whitelist |
| whiteListStatusChange |
Change Whitelist status for specified contact |
| getAddressBookImport |
Exfiltrate address book |
| deleteCallLog |
Delete call log by specified ID |
| setPhoneData |
Get configuration of the spyware |
| getWhiteSettingData |
Get Whitelist configuration: enabled/disabled answers or calls |
| getTelephone |
Get victim’s phone number |
| refresh |
Restart the Third stage |
| getAboutPhone |
Command is empty |
| searchAddressBook |
Search through the address book by specified phone number |
| SET_DEVICE_FUNC_SWITCH |
Enable/disable the spyware (master switch) |
| DELETE_ANSWER_CONVERSION |
Delete answered conversation by specified ID |
| getPhoneConversion |
Get conversation history by specified ID |
| getCallLog |
Get call log by specified type including the following information contact name, contact number, date, duration, type |
| deleteContacts |
Delete the phone number of the contact using specified ID |
Backend API list
/admin/user/activation-code
/admin/video-tutorial
/admin/user/review-ip-list
/admin/user/review-ip-address
/admin/zego-token
/admin/user/drop-down-list
/admin/device/alone/by/device-id/
/admin/device/alone
/admin/user/device/
/admin/user/device/sms-func/
/admin/device/call-log
/admin/device/call-log/all
/admin/update-remind
/admin/app-type
/admin/app-pack
/admin/app-pack/download/
/admin/app-pack/upload
/admin/video-tutorial/
/admin/operate-log
/sys-user/get-ip
/sys-user/login
/sys-user/user/change-password
/sys-user/user/logout
/sys-user/push-ip
/sys-user/device
/sys-user/device/batch-del
/sys-user/device/batch-recovery
/sys-user/device/force-del/
/sys-user/device/batch-force-del
/sys-user/device/
/sys-user/conversion
/sys-user/conversion/batch-update
/sys-user/conversion/status/
/sys-user/conversion/ars-status/
/sys-user/conversion/batch-del
/sys-user/conversion/duplicate-mc
/sys-user/conversion/batch-phone
/sys-user/blackList
/sys-user/blackList/batch-del
/sys-user/blackList/status/
/sys-user/blackList/duplicate-mb
/sys-user/user
/sys-user/user/status/
/sys-user/user/batch-del
/sys-user/user/logs
/sys-user/user/other-info
/sys-user/user/live/
/sys-user/user/audio-live/
/sys-user/apply
/sys-user/apply-state/
/sys-user/apply/batch-del
/sys-user/resetFrequency
/sys-user/answer-conversion
/sys-user/answer-conversion/batch-del
/sys-user/answer-conversion/status/
/sys-user/role
/sys-user/role/status/
/sys-user/menu
/sys-user/menu/status/
/sys-user/menu/batch-del
/sys-user/access
/sys-user/access/status/
/sys-user/access/batch-del