Malware successfully exploiting BNPL-apps
08 September 2022

Jump to
Confirmed fraud using BNPL-app
September 6th, ThreatFabric’s threat intelligence team has discovered multiple threat actors actively and unfortunately very successfully (confirmed stolen credentials) exploiting BNPL-apps such as ZIP by using Android banking trojans. Actors seem to focus on these accounts because buying expensive goods (PS5 or Vouchers) and sending them to a controlled drop site is one of the strongest laundering schemes. We expected that this would happen and now threat actors behind Android banking trojans are actively developing targeted malicious code against BNPL-apps. This attack is not limited to ZIP but all the popular BNPL-apps. The current BNPL-app attack where we have full visibility on is just very much focused on Australia at the moment but also have UK in their targets.
Fraud accelerators
No fraud control oversight by any payment or loan authority The lack of authority oversight is not limited to the soft or lack of credit checks executed today by BNPL providers, there is also no central bank or other authority forcing fraud protection controls on onboarding or loan authorisations which leaves the BNPL-providers with the full responsibility of implementing fraud protection while competing on easy/frictionless onboarding. They quicker, the easier, usually (less security and fraud controls) the better.
Limited KYC checks and digital identity proofing in an age of continuous data breaches BNPL providers performs limited digital and background identity proofing checks on the potentially stolen/leaked personal data and credit cards that are provided during registration of new accounts. In 2021, consumers lost almost $52 billion to traditional identity fraud and identity fraud scams, with nearly $7 billion attributed to new-account opening fraud (source: aite-novarica). The fraud is mainly caused by the continuous data breaches accelerating the use of syntactic IDs for new applications.
Without a strong Know Your Customer background checks and digital identity proofing fraud tools it is almost impossible to be in control of new-account opening fraud in 2022, this goes beyond BNPL providers, but considering their strong increase in users we expect that a real storm is coming to a group of users that already have hard time dealing with personal data (millennials). Historically fraudsters are always interested in where the most users are. Hence it is not difficult in this case what will happen and is already happening to BNPL-providers that are not regulated to have fraud controls in their online customer journeys.
Spoofable and hackable authentication controls Provide your phone number to receive a one-time code as SMS or provide your email to receive an activation link for registration. Or login with email and password to buy now pay with a syntactic id or a compromised account. There are many attacks that give access to codes received on a mobile device such as sim-swap attacks ore malware/spyware running on devices. Fully trusting these authentication controls is asking for fraud on your platform in 2022. Looking at BNPL onboarding and even loan consent journeys, they only thing I can conclude fighting fraud over 2 decades is that the lack of regulations have not triggered any fraud control by design. This means that the majority (it’s raining new BNPL-providers) must build in fraud after the fact (reactive). I am sure that will eventually lead to fraud related regulations on the loan consent journey (yes buying and paying later is a hard loan).
Over-trusting document and liveliness detection At some point in time (after fraud reports) some BNPL-providers adapted to what we see in other fintech sectors. The most interesting part is that none of these sectors want to learn from larger banks that have been working on improving fraud in their online customer journeys for at least 2 decades. The new trend seems to be what we see as over-trusting single-point identity proofing controls that usually have nothing to do with preventing fraud and are subject to proven hacks and bypasses by design, especially in the age of deep fakes, and 3d silicon masks.
In fighting fraud there is no silver bullet technology that protect you against all fraud vectors, it is usually a combination of multiple fraud detection sensors that are adapting to the threats on the customer journey. A very limited set of BNPL-providers have realised that it was too easy to onboard (limited identity proofing) and introduced digital validating of (potentially stolen or leaked) IDs and/or validating a liveness face matching control but seem to want to stay away from true biometrics such as faceid based authentication as much as possible in the customer journey. Before we discuss the weakness of this strategy of identity proofing it is good to understand that authentication controls are not equal to fraud protection controls.
The current document and liveness face detections are not very difficult to bypass with (3d) silicon masks or deep fakes or other AI tooling that is out there today. Hence over trusting this control to prevent syntactic id fraud should not be the only defence strategy. I have been actively involved in bypassing face liveness and document identity proofing tools in my previous business (penetration testing). What I find noticeable that we have always been able to bypass this type of solutions to some extent. This is also why most banks try to look at more fraud detection sensors today like the way a user interacts with his or her device (behavioural analytics using keystroke rhythms or swipes) and strong device id’s, location intelligence, hence continuously validating multiple fraud indicators. It seems fintech don’t want to learn from more than 2 decades of fighting fraud.
Attacks currently executed on BNPL including malware
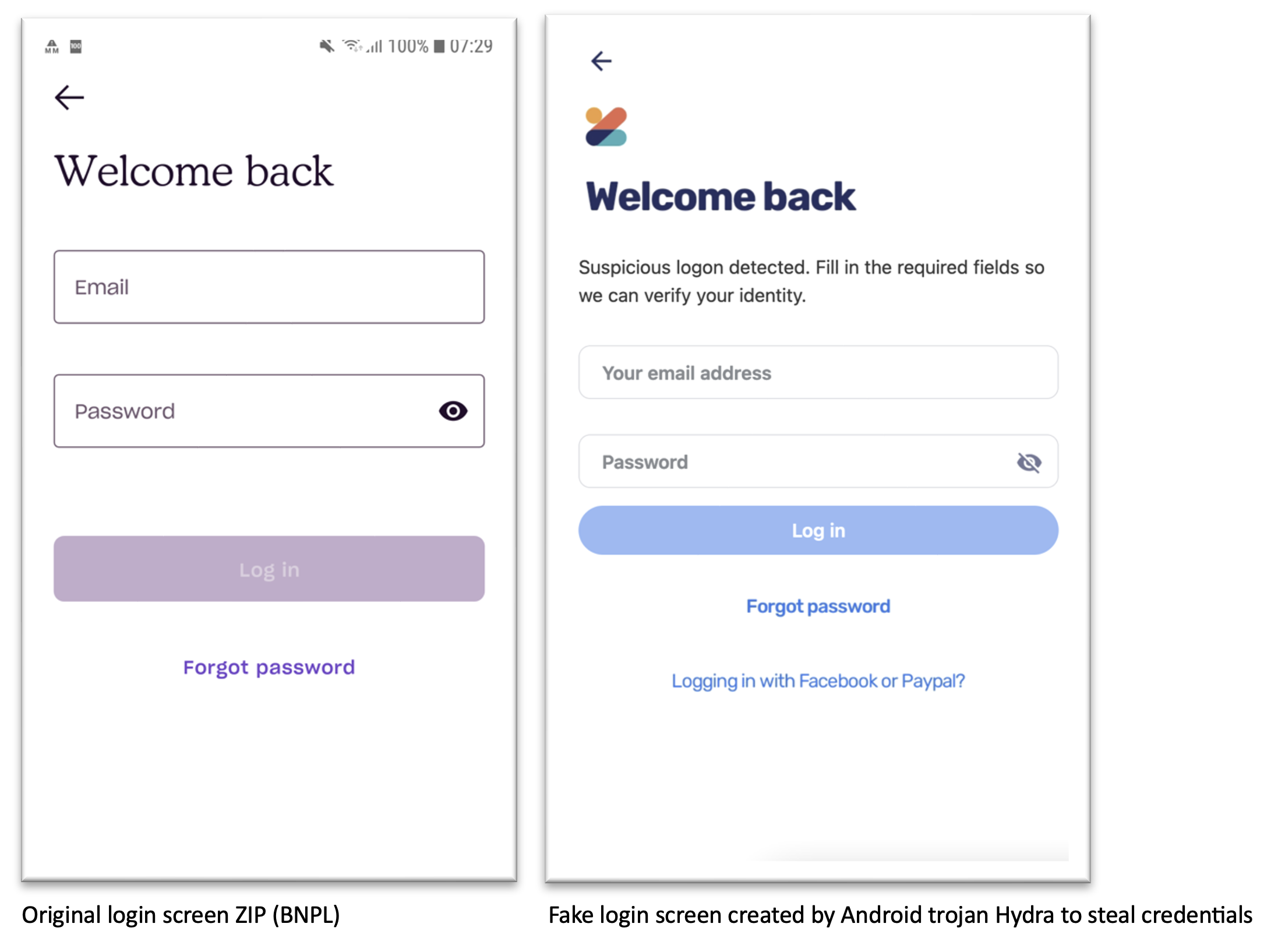
- Account Take Over (ATO) & On Device Fraud (ODF) by phishing and malware Less know by BNPL-providers or by none of the providers is that threat actors in the Android banking trojan threat landscape are currently targeting BNPL android apps with so called fake login screens to take over the victim’s account. A good example is shown below. With the original login and the fake login (overlay attack) Keystroke logger executed by Android banking trojan family Hydra (also distributed via the Google Play Store in July 2022) and Gustuff. This is a new fact none of the BNPL providers have any answer to due to the lack of a malware-based threat fraud detection SDKs inside their mobile apps.
- Great platform to launder money through expensive goods (PS5) The current modus operandi in Europe by voice phishers (Vishing) is to buying expensive goods because it is too easy in 2022 to setup a fake address or create drop locations (warehouses are even used). A fraudster is usually very aware of locations where there are no CCTVs and other physical controls so any online channel that is subject to new account fraud or account take over attacks allow fraudsters to buy goods with very slow response times on potential fraud are considered by design an entry point.
- Fake or fraudulent merchants resulting in false chargeback requests This is an attack vector that is less scalable but still a very big problem for most of this type of merchant and provider trust bounders with limited Know your Bank or in this case strong Know your Merchant background checks. Even banks with decades of fraud experience have a challenge here because it is not very difficult to participate as fraudulent merchant.
- New account fraud due to limited controls on know your customer (KYC) processes and overtrusting spoofable controlls such as liveness face detection and digital identy proofing uploaded by users or fraudsters. Fraudsters can buy (exfiltrate/launder) trough goods by sending it to a drop address. They worst part of this is that the victim will eventually find out but much later than in any other new account opening fraud attacks and can therefore not act on time
Recommendations
Don’t trust a single-point technology to prevent fraud on your customer journey, it’s a layered approach where strong authentication levels are your foundation, but don’t mix authentication with what is needed most in fintech’s easy onboarding journeys: multiple fraud indicators. In addition, don’t mix in easy with friction, fraud controls can be frictionless for a customer journey, in fact most of them have no impact on any onboarding or consent payment or loan flow.
An authentication foundation that is less subject to spoofing and bypasses Fraud fighting is about have multiple fraud indicators and good foundation as starting point. In the fight against fraud a good foundation is necessary. This base of this foundation is (hard) biometrics (multi factor authentication) on the customer journey such as FACEID to give consent on a login, loan or when adding or interacting with a credit card in your BNPL-app considering using the 3D secure protocol (risk-based authentication).
Layered fraud indicators (defence-in-depth) against every-changing fraud vectors
- Account take over attacks usually are abused by onboarding on a new device, in these cases location intelligence (IP, cell tower, AI based distance calculation) is an important fraud indicator. On top of that its important to bound a device to a user during the “easy” onboarding, at the moment in time the user interacts with your device create a strong fingerprint (DeviceID) that gives an indicator when crednetials are abused on another device. Also give the customer regular alerst on use of their device via preferable email instead of SMS considering the SMS store can be compromised by Android or IOS spyware.
- Syntactic ID fraud resulting in new-account fraud can be reduced but never be fully mitigated. Fighting fraud based on syntactic IDs starts with presenting your digital app developers with the awareness that you cannot trust a digital ID, address or any other information that is part of daily (reported and non-reported) data breaches. There are however ways to validate a digital identy using document identy proofing solutions that focus on font differences (and other mathers) or have a database of stolen leaked credentials. Our experience is that is the last control you should count on considering it is the easiest to bypass (its AI and blacklisting which is by design spoofable), but it always good to have it as additional fraud indicator. Another indicator could be liveness validation using face biometrics, however these as stated earlier also have limitations (3d) silicon masks and even deep fakes or other AI technologies. The best non-spoofable fraud indicator is the use of so-called behavioural analytics in the entire customer journey. Its not easy to spoof because the way a human interacts with his keyboard mouse or the way a person swipes on his phone is related to his or her cognitive behaviour. Usually, fraudsters have zero knowledge or cannot even adapt to the cognitive behaviour. A good example is your type flight (speed) between certain keys, statistically this is part of your (soft) behaviour. This is also how Threatfabric’s SDK detects account opening fraud as a result of syntactic IDs.
- Account Take over or Fraud On Device by malware As shown above ZIP is actively targeted by threat actors that are behind strong Android banking trojans families that are distribute to 40.000 users via benign apps (droppers) using the Google Play Store. None of the BNPL vendors we have spoken to are aware that this attack is even possible. Hence, we recommend to also add a malware threat fraud indicator sensor inside the BNPL mobile apps.
- Know your customer (KYC) and merchants They only way forward is asking regulators to not only focus on real-time credit checks but also forcing these platforms to introduce a strong authentication foundation in combination with a layered fraud indicator sensors and strong background checks on customers and merchants (KYC) to avoid fraudulent charge banks and transaction laundering in the form of high value goods (PS5 etc)