Shift Left on Fraud: Turning Fraud Management into Fraud Prevention
12 February 2026
Jump to
The Problem: Fraud doesn’t Start with a Transaction, it ends with one
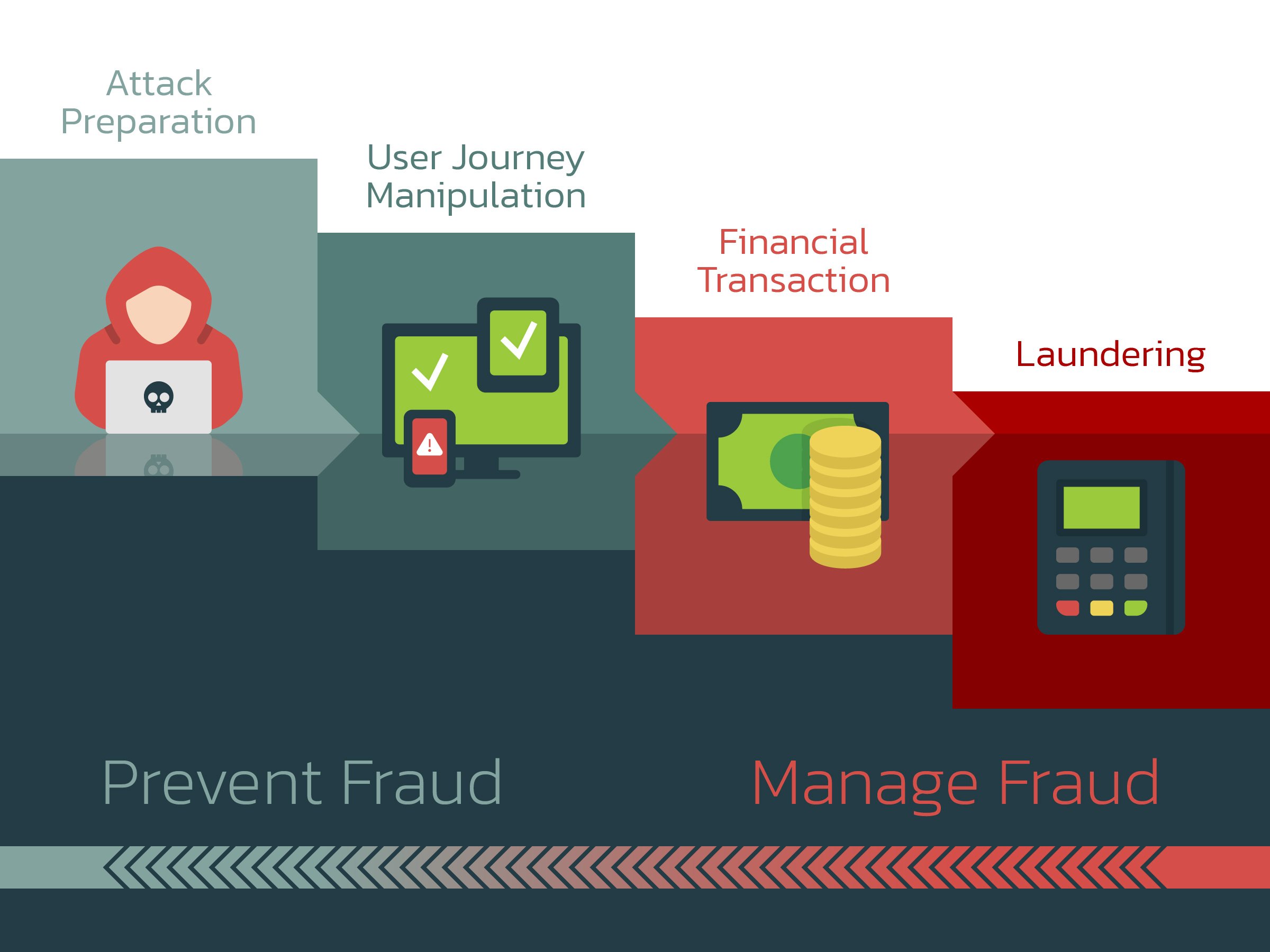
Financial fraud and scams don’t occur at a single moment in time—they unfold across a predictable lifecycle. Often, fraud and scam detection starts at the right‑most end of that lifecycle: the transaction stage. Most steps in the criminal process go overlooked.
By the time a fraudulent payment is initiated and signed, attackers have already prepared, manipulated the victim, compromised devices, or orchestrated mule accounts. Acting only at this late stage reduces detection accuracy, increases customer friction, and increases operational workload.
When a customer alerts you to a scam, speed and clarity are critical. What exactly happened? Is the transaction still in flight? Have the funds already been moved or laundered? Effective fraud management relies on immediate, high‑quality data to reconstruct events, support the customer, trigger automated follow‑up, and feed insights back into Detection and Fraud Intelligence teams.
Even when fraud is discovered post‑transaction, insights from earlier stages of the lifecycle dramatically improve your decision‑making, accelerate response, and strengthen feedback loops to prevent future cases.
Learn more on how we 'Shift Left on Fraud' with our products by downloading a detailed brochure:
GET BROCHURE
The Four Phases of Online Fraud

1. Preparation
Attackers organize campaigns, set up infrastructure, distribute malware, refine social engineering scripts, and prepare mule networks. Key questions answered at this stage include:
- Which campaigns are emerging?
- What malware families or TTPs are being prepared?
- Which accounts or infrastructures will be used?
2. User Journey
During the victim’s interaction with digital banking channels, early indicators of fraud surface:
- Device take‑over attempts
- Malware presence or RAT activity
- Remote control behaviour
- Suspicious navigation or behavioural anomalies
- Social engineering signals such as risky phone calls
3. Transaction
In this phase, the transactional and financial observables are taken into account. This is the phase where money is being moved to an account under control, or accessible by a criminal. It offers fraud managers detection opportunities, like:
- Transaction monitoring
- Velocity checks
- Payment profiling
While the transaction phase is where fraudulent money transfers are being attempted, 80 percent of the criminal process is performed in the previous stages.
4. Laundering
Money is moved through mule accounts and obfuscation paths. Shifting left aims to detect before this stage even begins.
Opportunities in Focusing on User Journey Intelligence
User Journey Intelligence is the richest – but often underutilized – source of pre‑transaction risk signals. Fraud and Scam Risk visibility throughout the entire journey dramatically boosts early detection.
ThreatFabric FRS offers key detection opportunities:
-
Detect Social Engineering Before Payment: Call‑intelligence signals (e.g., risky call duration, concurrent voice calls with login attempts) offer early indications of scam behaviour.
-
Detect Device & Malware Threats Before They Trigger Fraud:
- Mobile Malware: Heuristic detection of 100+ malware families.
- Remote Access Tools (RATs): Coverage for AnyDesk, Teamviewer and more.
- Call Intelligence: Detect indicators of vishing scams.
- Location Intelligence: Identify use of VPNs, TOR and location anomalies.
- Device Fingerprinting: Identify new and returning devices.
-
Behavioural Analytics as Early Identity Risk: Behaviour deviating from a user’s established pattern – or matching a known fraudster model – reveals high‑risk sessions even when credentials are correct.
-
Fully Privacy‑Preserving Signal Collection: FRS and behavioural indicators are GDPR‑aligned and processed without needing personal content.
With User Journey Intelligence, banks shift from “spotting a bad payment” to “spotting a bad session”. This pre-empts many fraud attempts.
Opportunities in Focusing on Threat Intelligence
Threat Intelligence (TI) – especially Mobile Threat Intelligence – helps banks understand and anticipate attacks before they even appear in their own environments. ThreatFabric’s MTI provides actionable, tactical, and strategic intelligence that is directly operationalizable.
Key opportunities:
-
Anticipate Campaigns Before They Hit Your Bank: TI reveals campaigns, distribution methods, malware capabilities, and command‑and‑control behaviour in advance.
-
Understand Emerging TTPs: Preparation‑phase TTPs indicate how fraudsters will manipulate user journeys, enabling pre‑emptive defense tuning.
-
Strengthen Threat Protection & Device Risk: TI insights feed not only fraud detection engines but also mobile‑app protection layers, related to Malware, RATs and Device Risk.
-
Build a Closed Feedback Loop: With Threat Intelligence you build a feedback loop with FRS Fraud Metrics. TI creates an intelligence‑reinforcing cycle for continuous improvement.
Technology: Leveraging TI & FRS for Pre‑emptive Detection
How to Leverage Threat Intelligence (TI) in Detection:
- Map malware families and capabilities to detection rules
- Flag sessions where malware signatures match known indicators
- Pre‑configure detection for imminent campaigns detected globally
- Monitor attack‑risk perspective (campaign intent, delivery vectors)
How to Leverage Fraud Risk Suite (FRS) in Detection
FRS User Journey Intelligence can be used in any Risk or Decisioning engine. It adds fidelity and depth to risk signals, and offers traceability from transaction ID’s into the User Journey and its risk signals:
- Device Risk Signals: RAT detection, device compromise, malware presence
- Behavioural Analytics Signals: motion anomalies, keystroke anomalies, identity deviations
- Attack Risk Signals: threat‑intel–driven detonations of campaign patterns
- User Journey Scoring: combined risk model built from early‑stage indicators
Together, TI + FRS form the technical backbone needed to truly shift left.
Benefits of Shifting Left
Based on the combined insights across your events, shifting detection earlier yields:
✅ Higher detection rates & fewer false positives
Earlier signals enable stronger contextual scoring and more confident decisions.
✅ Lower operational impact on fraud cases
Preventing fraud at the journey level avoids costly investigations and recoveries.
✅ Compliance with consumer‑protection regulation (PSD2/PSD3/PSR)
Early‑risk identification aligns with regulatory pushes for scam prevention and strong customer protection.
✅ Privacy‑preserving detection
Behavioural and device‑risk indicators follow strict privacy‑by‑design principles, based on consumer protection, minimizing PII processing, ISO Certification, and Model Transparency.
Conclusion
Fraud prevention shouldn’t just be about asking “Was this payment fraudulent?”. It’s about asking “Was this session risky, and why?” and “Is this campaign coming to our Online Channels?”.
Banks that shift left—from Transaction to User Journey to Preparation—transform their approach from reactive fraud management into pre-emptive, intelligence‑driven fraud prevention.
By combining Threat Intelligence and the Fraud Risk Suite, organizations gain the earliest possible visibility into attacker behavior, user manipulation patterns, and device‑based threats. This leads to:
- fewer victims,
- less operational workload,
- better customer experience, and
- stronger compliance posture.
Shifting left isn’t just a strategy—it’s a competitive advantage in the future of fraud defense.