Exobot v2 update - staying ahead of the competition
01 July 2017
Jump to
Abstract
In the last couple of months since our previous blog on Exobot we have seen many different samples of the Exobot v2 Android banking malware pass by. They have been busy developing new features for the bot to stay ahead of their competition. Several of the changes in the bot we have seen are interesting enough to warrant a new blog post, so here we go!
Modularity
The most interesting feature that has been added to Exobot (in our opinion anyway) is the module system. When the bot is started for the first time it will first try to obtain the “main” module from the C2 server and will not do anything until it gets this module. After the module is retrieved it is saved in the private app storage (/data/data/packagename/) and loaded by a DexClassLoader. The “main” module provides most of the default bot functions:
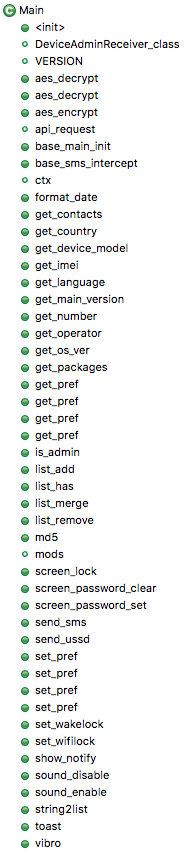
Main module functions
After the main module is loaded the bot will keep polling the server for additional modules to load (so far none are returned). Having this module system makes it easier to hide functionality (since it is not present in the bot by default) and sell pieces of functionality seperately. An example of another module could be one with socks proxy capabilities.
Socks proxy
All strings used in the Exobot code are obfuscated. Going through all these strings we noticed recent additions hinting to the implementation of a socks proxy:
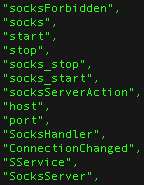
Socks proxy related strings
Previously we’ve only seen hints of a socks proxy in the C2 code. This proxy functionality could make it easier for attackers to stay hidden and bypass ip-based fraud detection. So far the strings are not used in the current code, possibly indicating that the proxy code is placed in a module.
Network traffic encryption
Network traffic has received an upgrade in the form of an encryption layer. All requests and responses (except for the module download) are now encrypted using AES/ECB/PKCS5Padding and then base64 encoded:

Encrypted HTTP traffic

Decrypted HTTP traffic
The encryption key is a hex encoded MD5 hash of a string located in the same location as the other obfuscated strings (so far set to “not-cache”). Note that the “Cache-Control” header in the request is also set to this same value, making it easier to obtain it. Exobot v2 is the only Android banking malware with an additional encryption layer above TLS.
Additional obfuscation
Some Exobot samples seem to have included additional obfuscation in the form of a loader: The original application’s classes.dex file is encrypted and included as an asset file. When the Android app is started the loader decrypts the asset and uses a DexClassLoader to load the classes.dex and replaces the loader application with the unpacked application. This makes it a lot harder for static analysis tools to detect the malware and manual analysis takes more time. The loader is fairly easily recognized by the asset file (*.dat), the type of code obfuscation used and the fact that it implements a custom Application class to do it’s magic as soon as the app is started.
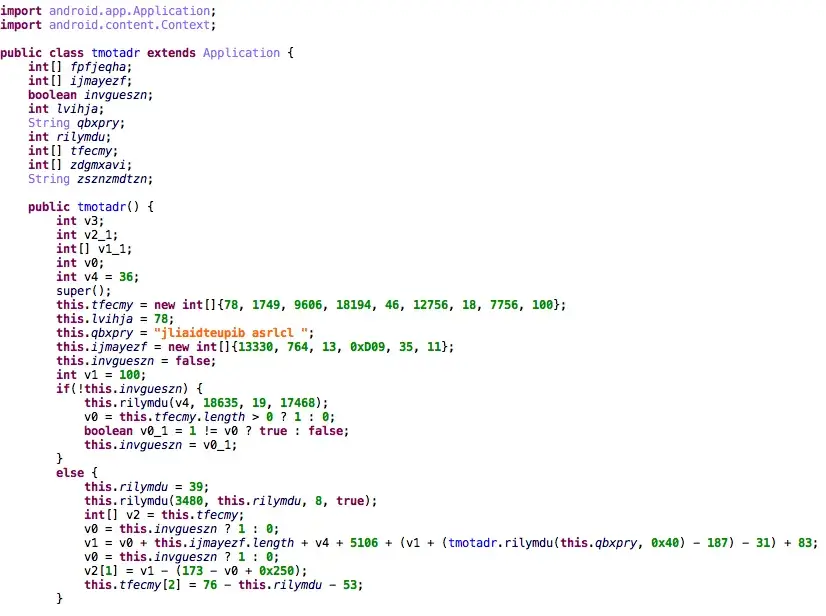
Obfuscated loader code
Samples with loader
1cd3095b176520e4bf7d3fa86ec91e852ee93b2172c8bd3113f91e2569a7c481 (10 Jul 2017) ca2cc26e81196a2031a5cdeda91a6624ba9d34e03e5b1448dd682b0215134d15 (10 May 2017) 77e26712490e8ec681881b584c5e381af0dcece21f0dcfa483661f125a399a2d (25 Apr 2017) 8e9bdb1f5a37471f3f50cc9d482ea63c377e84b73d9bae6d4f37ffe403b9924e (21 Apr 2017) ca859564cfbfca3c99ab38c9cb30ad33ec9049fe67734bae9d9b69cd68845188 (17 Apr 2017) 59ada6b530bd2c7c15d8c552c7ebf3afcc14976bfa789a6e2c2fca3e354baab0 (11 Apr 2017)
For sale through a public website
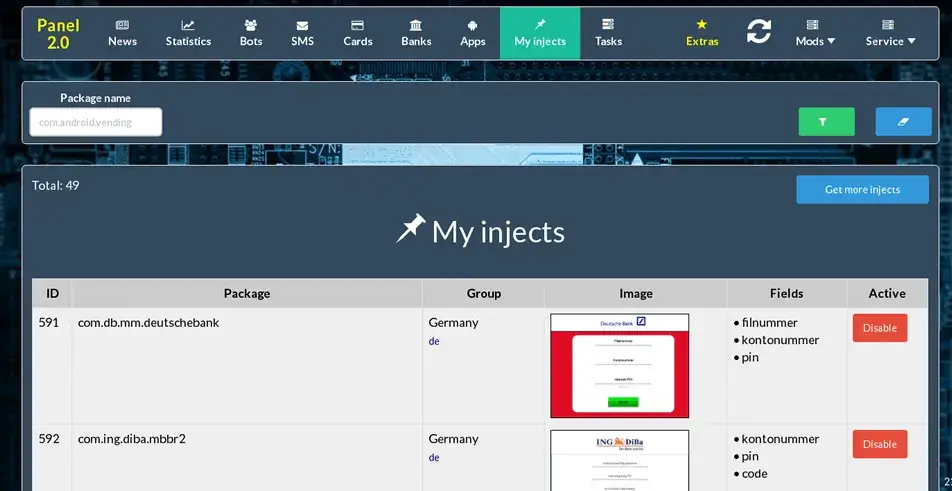
Another noticeable change in tactics seems that the actors behind Exobot are selling their service using publicly available website, including screenshots of their Panel.
Public website selling Exobot

Web injects in the Exobot panel
Latest samples
c1ef19c9abc479070d7841846ff6b4c973b34b2035428b50999ebe63eb0547db (25 Jul 2017) da68cc23a89c2b794827e9f846ed5d1e371a1c14229696bc46a4d9ec380425d4 (25 Jul 2017) 498304e3f60abe29bb06661b21e579d5a25f104eb96ebf0d5d573ce9f8308b89 (19 Jul 2017) 690310a635b5c82c28a76332b83a7b34b8604e822ed8f8e4eb1f0be85c177c62 (16 Jul 2017) ae4ed005f891101b297689530e9d07068e0a0779c7a03abe36f30b991b065ff9 (15 Jul 2017) c28b6346d59a828ce319e94d08c35b530ae39fd5801d17e6f84a02a592621e2d (10 Jul 2017) 1cd3095b176520e4bf7d3fa86ec91e852ee93b2172c8bd3113f91e2569a7c481 (10 Jul 2017) b8b424866ba77728034e231f295399f523154accf587424c9d42cbb1c8edba9e (09 Jul 2017) 92c560d55ac0943022be38404fee8fd70da53cca33d7e340ea98712af389f780 (07 Jul 2017) 856d1f7cf037e031dda4accc3454d84115bc91be488b74817580e541be6abbad (04 Jul 2017) 2d1d9cabf564bc9c3a37c21cd98c7c045453dc583fab4479fe12d8e4e70f339a (25 Jun 2017) f6851790dc811b3a9acc425730ffeaab49c5cde4cb0a39cfcc659c4d29c908ad (22 Jun 2017) 10931ae2c165d4786fdd9585c419a6b1d2dd07d96242d26d23daab14d684f4e0 (21 Jun 2017)
Follow our threat hunters @ThreatFabric for updates.
Protect your Android users
CSD for Android is an Android library that can be integrated easily into any existing Android app. One of the features of the library is that it will detect overlays that are projected over the running app (malware attack vector). Request a white paper for more details.