Investment Scams vs Fraud Kill Chain
24 April 2024
Jump to
This fourth episode covers one of the most diverse scams: those offering an online investment opportunity. Criminals use a wide variety of methods suiting their logistical capabilities and skills. Some investment scams start as romance scams before turning to “investment”.
The unflatteringly named “Pig Butchering” scams are an example of this. Others use some kind of “impersonation” of an official-sounding organisation. Many investment scams start as an advertisement or "clickbait article" on social media, with claims that seem too good to be true, such as "Let me tell you how I earn 20,000 dollars per month." Some professionals believe social media scams and investment scams are synonymous.
This blog is part of a series that aims to provide tools to check your fraud detection capabilities for readiness against the most prolific fraud and scam types. From malware campaigns to scams, we'll analyze tactics, techniques, and procedures (TTPs), kill-chain mappings, and detection gaps.
The Problem
Investment scams are highly diverse and often begin with one of these methods:
- Impersonation,
- Romance,
- Spamming,
- Social Media ads or articles.
Scammers then guide the victim toward their true goal: a fake investment opportunity. This process can sometimes take weeks or even months.
These "opportunities" typically involve:
- Social Media: Scammers use platforms like Facebook, Instagram, and Twitter to promote fraudulent investment opportunities, often using images of luxury items to entice people.
- Fake Investment Platforms: They create professional-looking online platforms featuring fake customer reviews and logos to appear legitimate.
- Email and Text Scams: Unsolicited emails and texts are sent to potential victims, offering high returns on investments.
- Crypto and Forex Scams: These scams offer investments in binary options, forex, and cryptocurrencies with promises of high returns. Scammers may distort prices on their websites or refuse to return the invested funds.
- Phishing Websites: These are fake websites that mimic legitimate investment firms, designed to steal personal information and financial details.
Our research indicates that 12 percent of scams can be classified as investment fraud. However, a significant number of social media and romance scams may also have an investment scam component.

About the Fraud Kill Chain
With the right tools, anti-fraud teams should be able to pick up the tell-tale signs of these attacks. The Fraud Kill-chain is a useful tool to identify detection opportunities and gaps. It allows anti-fraud teams to map capabilities to attacks and helps control various frauds and scams.
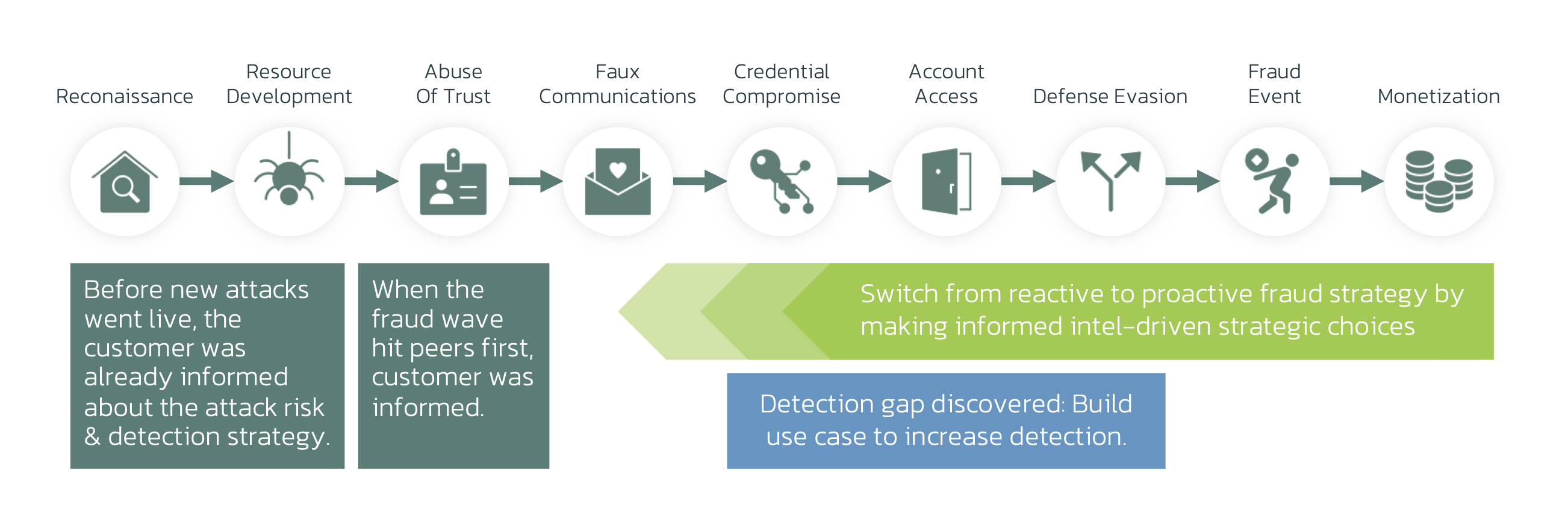
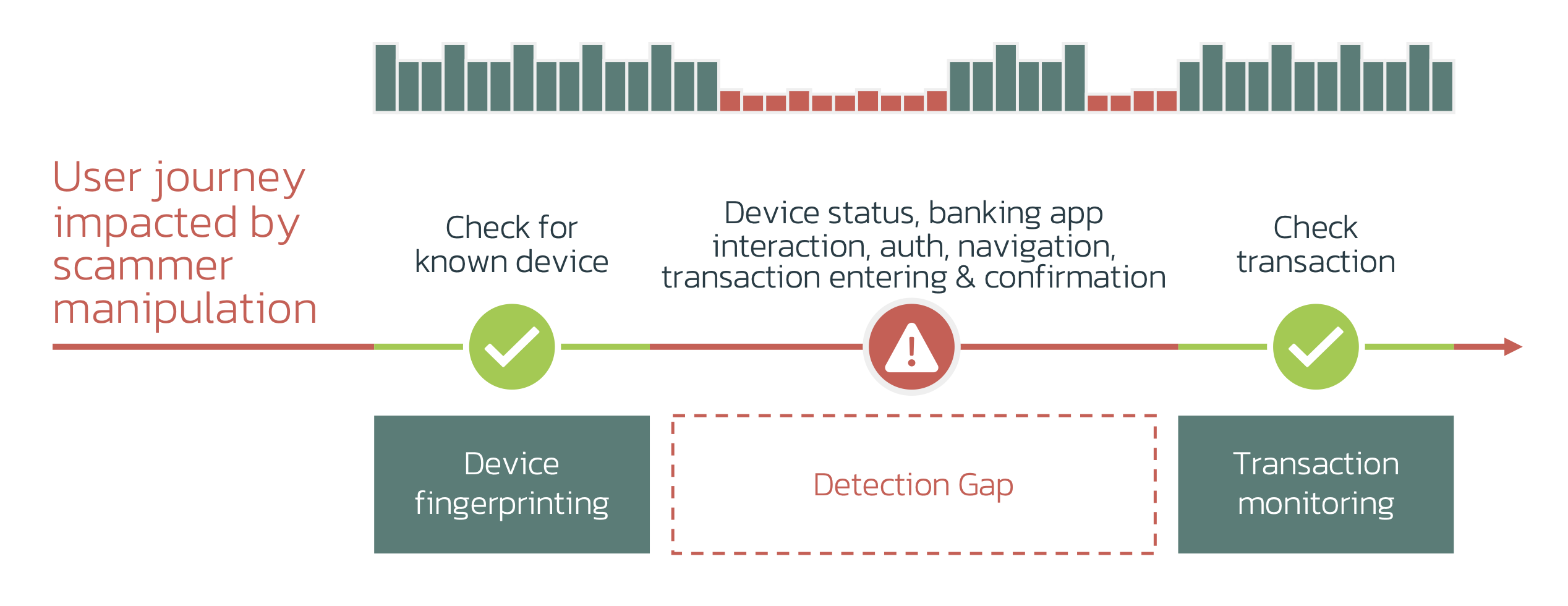
Many investment scams have few technical TTPs during the crucial phases of credential compromise, account access, and defense evasion. These phases typically offer the best opportunities for detection in online channels. Since these scams lack distinctive technical markers, behavioral models can be a highly effective alternative.
Investment Scams vs Fraud Kill-Chain

Detection Gaps & Opportunities
Gap 1: Behavioral Biometrics
When criminals take control of an account, their behavior differs from the legitimate user’s. Behavioral biometrics can translate these behavioral TTPs (tactics, techniques, and procedures) into risk signals. It’s crucial to use multiple models to assess these signals:
- The "attack" perspective: This focuses on spotting manipulation, pressure, and hesitation.
- The "individual use" perspective: This detects when a customer's interaction with the device is "different from normal."
Gap 2: Multi-Channel and Correlation
By correlating Device Risk and Behavioral Risk, you can correlate “on-call” with “active RAT” with “behavioral risk”. Your capabilities should include visibility on both web and mobile channels, as scams often move from one to the other during the attempt.
Conclusion & Takeaways
As scammers rake in billions, anti-fraud teams should perform the following checks:
- Ensure Visibility: Ensure you have visibility on both mobile and web channels. It's important to monitor the entire user journey, not just the login and transaction points.
- Correlate Risk Signals: Verify that you can correlate risk signals across multiple online channels and technologies, including device risk and behavioral risk.
- Stay Updated: Keep up with the threat evolution with mobile threat intelligence.
Detection Readiness Workshop
ThreatFabric helps banks and financial institutions worldwide perform these analyses. If you’re interested in a detection readiness workshop, we're here to assist.